Displaying items by tag: Virus
How to Repair Corrupt Outlook Data File (PST)?
Personal Storage Table or PST is a popular and most commonly used mailbox data file format for storing, backing up, and migrating mail items to and from Microsoft Outlook.
XDR round-up 2023: High-severity threats on the rise, peak during holidays
GUEST RESEARCH: In 2023, Barracuda XDR, including its team of SOC analysts on 24-hour watch, cut through nearly two trillion (1,640 billion) IT events to isolate tens of thousands of potentially high-risk security threats.
How To Get MS Outlook Data Repaired From a Vvew Virus Attack
Several people lose their Microsoft Outlook data because of Vvew virus attacks. Many people are unaware of the solutions to this problem and ultimately lose important information. At the same time, this is all they need to recover their files.
It is essential to note that the Vvew virus is an Avant virus that attacks computers through emails and website pages. It has layered blocks of designs used to attack, encode, and erase MS Outlook PST files. Once it strikes any .PST file, it alters its code and changes its extension to .vvew. Once this happens, you cannot use your Outlook files or mail because your MS Outlook reads files with .PST and OST extensions.
While the Vvew virus might seem harmful to files and data, the Recovery Toolbox for Outlook has powerful algorithms to scan every file from the email box and repair it. There are two methods to solve the problem with this tool. They are:
- The online method: https://outlook.recoverytoolbox.com/online/
- The offline method: https://outlook.recoverytoolbox.com/repair-outlook/
The two methods are workable to solve the virus attack because the tool has an online and offline version. You can use these versions to recover encrypted .PST files (.PST across all versions– ANSI (Outlook 97-2003), Unicode (2007 and above)).
Read through to understand how to recover and restore your Microsoft Outlook files.
The Online Method: How to Recover Your PST File with Recovery Toolbox for Outlook
You can easily use this to regain your affected information online. This recovery process works effectively on all devices as smoothly and swiftly as possible to restore OST files and fix your encrypted .PST files.
Follow these steps to repair your files online:
- You must change the file extension from Vvew to PST for the service to select the recovery algorithm to use.
- Click “Select file” and select an Outlook data file with the extension “.PST” or “.OST.”
- Input your valid email address
- Click Continue
- Wait for the corrupted .pst/.ost file to be recovered
- Download the recovered Microsoft Outlook pst file
Once you have recovered the data from the affected MS Outlook file, it will be stored as a new MS Outlook 2016 file with the .PST extension. This way, it will be easy to regain any .PST MS Outlook private file through any browser and device.
The Offline Method: How to Recover Your Infected .PST with Recovery Toolbox for Outlook
Before you begin, you must look for your Outlook Data Files in Outlook before repairing infected .pst files. Follow these steps
- First, select File, Choose Account Settings, and Click Account Settings.
- Next, select the Data Files
- You will see all Outlook Data Files (.PST) and Offline Data Files (.OST) listed, along with the account name the files are associated with.
Once you have been able to locate all your Outlook files, take these steps to repair your attacked file.
Step 1. Identify the infected Outlook data file location
To recover an infected Outlook data file, first Exit Microsoft Outlook and check one of these locations:
- For Outlook 365: C:\Users\Username\AppData\Local\Microsoft\Outlook\
- For Outlook 2019: C:\Documents and Settings\user\Local Settings\Application Data\Microsoft\Outlook
- For Outlook 2016: C:\Documents and Settings\user\Local Settings\Application Data\Microsoft\Outlook
- For Outlook 2013: C:\Documents and Settings\user\Local Settings\Application Data\Microsoft\Outlook
- For Outlook 2010: C:\Documents and Settings\user\Local Settings\Application Data\Microsoft\Outlook
- For Outlook 2007: C:\Documents and Settings\user\Local Settings\Application Data\Microsoft\Outlook
- For Outlook 2003: C:\Users\username\Documents\Outlook Files\
- For Outlook XP: C:\Documents and Settings\Username\Local Settings\Application Data\Microsoft\Outlook
- For Outlook 2000: C:\Documents and Settings\Username\Local Settings\Application Data\Microsoft\Outlook
Step 2: Download, install the program and Run it.
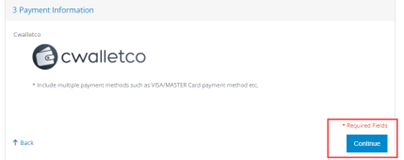
Step 3: Choose the file encrypted by the virus and select Next.
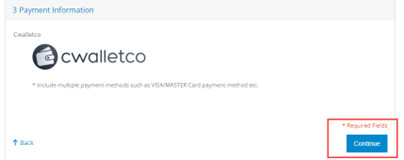
Step 4: Select Recovery Mode and Click Next.
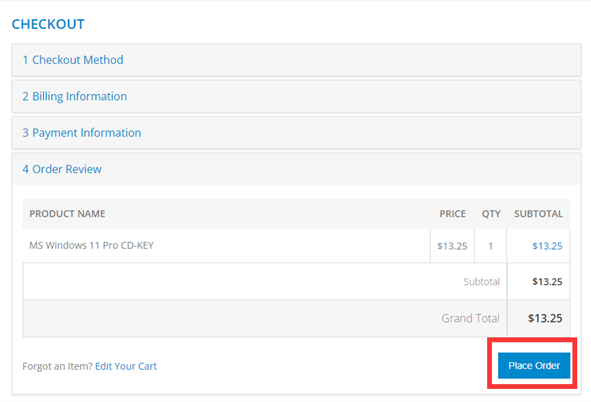
Step 5: Click on Yes to begin recovery.
Step 6: Inspect the data preview and click Next to save the recovered file to a new location.
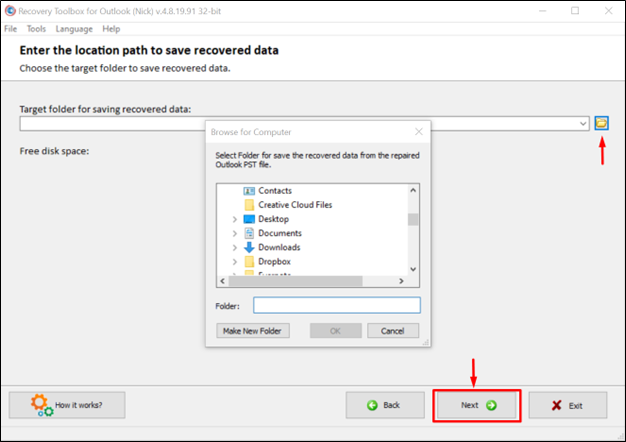
Step 7: Enter the location to save the .pst file and click Next.
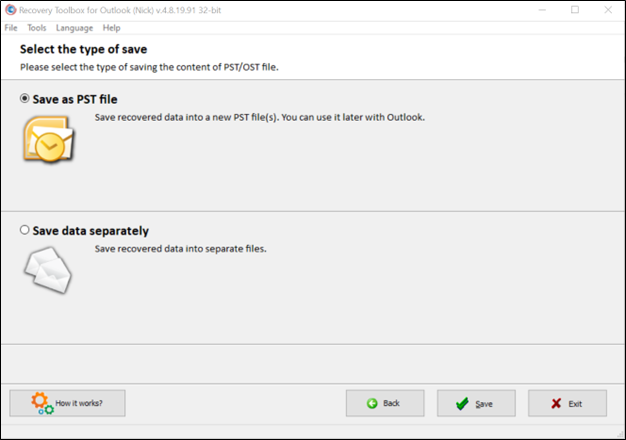
Step 8: Save the recovered data as the new .pst file.
Step 9: After checking the successful recovery results, click Finish to exit the Recovery Toolbox for Outlook tool.
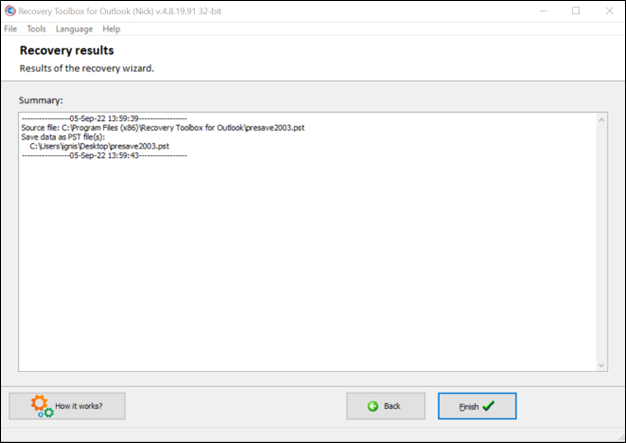
It is important to note that you should substitute the damaged file with a recovered one. You can also add the recovered .pst file to the list of data files in Outlook. This is how you do it for these versions of Outlook: 2021, 2019, 2016, and 2013:
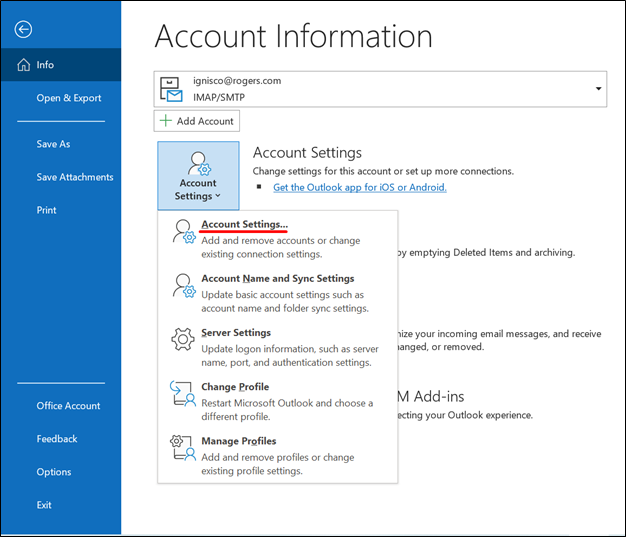
- Choose the menu item File | Info.
- Next, click the button Account Settings.
- Finally, choose Account Settings in the pop-up menu.
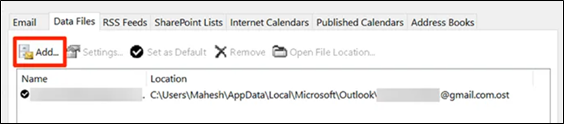
- Choose the Data Files tab and click Remove.
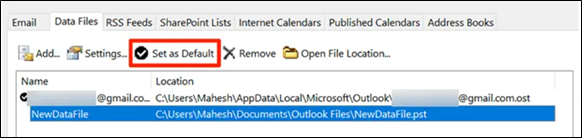
- Click Open File Location and select the recovered file. Click Set as Default.
Once you have reached this stage, you have successfully fixed the issue.
Conclusion
The Recovery Toolbox for Outlook uses high-grade algorithms and procedures in analyzing, fixing, and restoring files, irrespective of the problem or its cause– i.e., viruses, bugs, hardware damage, network problems, HDD damage, etc.
The tool has the following advantages:
- With the tool, you can fix Microsoft Outlook files with .PST extension across different versions (ANSI (Outlook 97-2003), Unicode (2007 and above)).
- The recovery tool allows you to repair and recover files protected by a password.
- With the tool, you can recover damaged (or attacked) OST files irrespective of their versions.
- The tool allows you to repair encrypted files with the .PST extension.
- You can quickly repair PST files of different sizes, up to 180 Gigabytes, and more.
The Recovery Toolbox for Outlook is very efficient for repairing and recovering every kind of file and data on Microsoft Outlook. You can use it to easily access damaged, password-protected, and encrypted files like contacts, tasks, documents, etc. The tool is easy to use and is effective both online and offline.
How adult content, streaming, and video hosting subject users to security risks
Adult content, streaming, and video hosting sites pose the most security and privacy threats—malware, intrusive ads, and trackers—according to research conducted by cybersecurity company NordVPN.
iTWireTV Interview: Mark Gorrie, NortonLifeLock APAC MD, talks Norton 360 Advanced, two new Cyber Safety report and more
GUEST INTERVIEW: Internet security software is a vital component of online life today for all your devices, with Norton 360 Advanced also including identity theft insurance for the first time, and with cyber scammers more cunning that ever before, we look at the findings of two new Cyber Safety Insights and Pulse reports focusing on child safety and the latest scams afflicting us all.
VIDEO Interview: Mark Gorrie, NortonLifeLock APAC MD, talks Norton 360 Advanced, two new Cyber Safety report and more
GUEST INTERVIEW: Internet security software is a vital component of online life today for all your devices, with Norton 360 Advanced also including identity theft insurance for the first time, and with cyber scammers more cunning that ever before, we look at the findings of two new Cyber Safety Insights and Pulse reports focusing on child safety and the latest scams afflicting us all.
Impersonation scams still plague consumers
Consumers have been warned about ongoing scams where scammers are impersonating well-known telecommunications or tech companies like Telstra, NBN Co and Microsoft.
Next Telecom wins SonicWall Emerging Partner ANZ 2022 award
COMPANY NEWS: Next Telecom is excited to have been named the SonicWall ANZ Emerging Partner for 2022. The SonicWall partner awards recognise the achievements of SonicWall partners in the pursuit of excellence in the rapidly evolving Cyber Security landscape.
iTWireTV Interview: Aaron Bugal of Sophos talks cyber security implications of returning to the office, and more
Returning to the office is something many more people have done since lockdowns ended, but which devices are unpatched and unprotected from not being used for months? Cyber security has never been more important, with Aaron Bugal, Global Solutions Engineer at Sophos, telling us all we need to know.
VIDEO Interview: Aaron Bugal of Sophos talks cyber security implications of returning to the office, and more
Returning to the office is something many more people have done since lockdowns ended, but which devices are unpatched and unprotected from not being used for months? Cyber security has never been more important, with Aaron Bugal, Global Solutions Engineer at Sophos, telling us all we need to know.
VIDEO Interview: A 'fireside chat' with Sophos ANZ MD John Donovan as we discuss the 2022 Threat Report
GUEST INTERVIEW: Sophos has released its 2022 Threat Report, and Sophos ANZ MD joined iTWireTV not only to tell us its findings, but to recap 2021, talk ransomware, ethical zero-day research and more!
iTWireTV Interview: A 'fireside chat' with Sophos A/NZ MD, John Donovan, as we discuss the 2022 Threat Report
GUEST INTERVIEW: Sophos has released its 2022 Threat Report, and Sophos A/NZ MD joined iTWireTV not only to tell us its findings, but to recap 2021, talk ransomware, ethical zero-day research and more!
Telstra launches two hour delivery service in selected Sydney, Brisbane and Melbourne stores
A series of participating Telstra stores in Sydney, Brisbane and Melbourne are letting customers take advantage of Telstra's new two hour delivery service to coincide "with the latest handset launches," but Canberrans, who are also in lockdown, miss out.
BlackBerry's security teams sees old dog threat actors learning toxic new tricks after all
BlackBerry’s Research and Intelligence has released its "Old Dogs New Tricks" research paper which examines how threat actors are sneakily leveraging new and uncommon programming languages to evade detection and hinder threat analysis.
Reflecting on the year of the remote worker
2020 was both challenging and disruptive for everyone. In Australia, just when we’d become optimistic about the economic and societal recovery after the devastating summer bushfires, the COVID-19 pandemic struck. For most organisations and their employees, two words summarise the year that unfolded as a result—remote working.
Hold for the operator: Why the COVID-19 crisis has made contact centre agents more important than ever
GUEST OPINION by Brendan Maree, Vice President Asia Pacific, 8x8: In challenging times, an experienced, well trained contact centre team can be an invaluable asset to your organisation.
- contact centre agents
- Contact centres
- COVID 19 crisis
- Brendan Maree
- 8x8
- Pandemic
- Telstra
- Services NSW
- shutdown
- restrictions
- Virus
- financial institutions
- Utilities
- Robotic automation
- Chatbots
- Interactive Voice Response
- Call centres
- Business
- Australia
- Call centre operators
- Australian Banking Association
- new business
- consumers
- Investment
- Economy
Hold for the operator: Why the COVID-19 crisis has made contact centre agents more important than ever
GUEST OPINION by Brendan Maree, Vice President Asia Pacific, 8x8: In challenging times, an experienced, well trained contact centre team can be an invaluable asset to your organisation.
- Contact centres
- contact centre agents
- COVID 19 crisis
- Brendan Maree
- 8x8
- Pandemic
- Telstra
- Services NSW
- shutdown
- restrictions
- Virus
- financial institutions
- Utilities
- Robotic automation
- Chatbots
- Interactive Voice Response
- Call centres
- Business
- Australia
- Call centre operators
- Australian Banking Association
- new business
- consumers
- Investment
- Economy
GreyScan, University of Tasmania collaborate to develop COVID-19 environment mobile trace detection tool
Australian technology company GreyScan is partnering with the University of Tasmania to develop a mobile trace detection tool to "rapidly and accurately detect" coronavirus and other surface viruses in the environment.
- GreyScan
- University of Tasmania
- coronavirus
- COVID19
- Environment
- trace detection tool
- surface viruses
- Virus
- CSIRO
- CSIRO Innovation Connections Grant scheme
- Samantha Ollerton
- mobile virus detection device
- Professor Michael Breadmore
- environmental testing
- Grey Innovation Group
- Scientific research
- Australia
- Peter Dinham
WEBINAR INVITE from TDL: Life after Lockdown: Reimagining the Modern Workplace
WEBINAR INVITE from TDL: As we emerge from lockdown, the workplace will look very different and long-term remote working is likely to feature heavily. While some workers will be counting the days until they can head back to the office, others will be wishing they could stay in their home offices permanently.
WEBINAR INVITE from TDL: Life after Lockdown: Reimagining the Modern Workplace
WEBINAR INVITE from TDL: As we emerge from lockdown, the workplace will look very different and long-term remote working is likely to feature heavily. While some workers will be counting the days until they can head back to the office, others will be wishing they could stay in their home offices permanently.
WEBINARS & EVENTS
- UiPath to Unveil Latest Agentic Automation Solutions at Agentic AI Summit
- ALL WELCOME - 6 DAYS TO GO - AI in Action is your opportunity to gain actionable strategies for deploying scalable, reliable AI solutions that drive measurable business outcomes.
- TODAY FREE VIRTUAL EVENT - EXL SERVICE, AI in action Driving the shift to scalable AI
- Expert warns: Small businesses missing out on AI cost-saving and growth opportunities
- Datadog Opens Registration for Its 2025 DASH Conference
CYBERSECURITY
- Can cyber security be a platform for innovation and growth?
- 5 Reasons You Should Consider Hiring a Cyber Security Professional For Your Business
- Cloudflare Advances Industry’s First Cloud-Native Quantum-Safe Zero Trust Solution
- Nozomi Networks Named to Fast Company’s World’s Most Innovative Companies 2025 List
- Cybersecurity for Small and Medium Businesses in 2025: Challenges and Solutions
PEOPLE MOVES
- Tenable Appoints Scott Magill as Country Manager for Australia and New Zealand
- Dirk Vorster Joins Wild Tech to Strengthen Business Development and Industry Alliances
- SAP expands ANZ leadership with two key appointments
- DataSnipper appoints Siu Wei Lee to lead Asia Pacific expansion
- Zetaris, The Modern Lakehouse for AI, Continues its Global Expansion with Appointment of Robert Herjavec as Executive Director Global Strategy
GUEST ARTICLES
- Dryad Networks demonstrates first fully functional drone prototype for detecting, locating, and monitoring wildfires
-
SevenRooms unveils new AI features to power ‘SuperHuman Hospitality’, ‘helping restaurants’ personalise, streamline & save time
AI Responses, AI Feedback and AI Note Polish are giving…
- New Research Shows Parents Prone to this Common Scam
- How AI can supercharge your productivity at work in 2025
- SOTI and Urovo Partner to Combat Device Downtime with Proactive Battery Management and Remote Support
- Unlock online freedom with a free VPN
- AI and the Future of Insurance: Why Solving the Data Integration Challenge Matters
- What are haplogroups, and how do they connect with ethnicity?
- Why Missouri car accident victims should act fast to protect their legal rights
- What to bring to your first meeting with a Florida personal injury lawyer
Guest Opinion
- New Research Shows Parents Prone to this Common Scam
- How AI can supercharge your productivity at work in 2025
- Unlock online freedom with a free VPN
- AI and the Future of Insurance: Why Solving the Data Integration Challenge Matters
- What are haplogroups, and how do they connect with ethnicity?
- Why Missouri car accident victims should act fast to protect their legal rights
- What to bring to your first meeting with a Florida personal injury lawyer
-
How to prevent tool wear and damage in CNC Aluminum Processing
GUEST OPINION: In the world of precision manufacturing, maintaining the…
- Anti Scam Investment Much Needed
- Govt must Incentivise People Initiatives to Beat Productivity Slump
ITWIRETV & INTERVIEWS
- Amazon CISO CJ Moses gives rare interview
- Matt Salier explains the Australian Cyber Collaboration Centre's voluntary data classification framework
- Qualys CEO Sumedh Thakar explains the Risk Operations Centre (ROC)
- iTWire talks to SailPoint about identity management in the Enterprise
- How Blue Yonder is applying AI and innovation to solve supply chain challenges
RESEARCH & CASE STUDIES
Channel News
Comments
-
Re: iTWire - Why Software Developers Need a Security ‘Rewards Program’
For most developers the security/performance trade off is still the hardest one to tackle, even as the cost of processing[…]
-
Re: iTWire - The Risc-V architecture that can shape the future of computing
RISC has been overhyped. While it is an interesting low-level processor architecture, what the world needs is high-level system architectures,[…]
-
Re: iTWire - Is Linux finally ready to storm the mainstream?
There are two flaws that are widespread in the industry here. The first is that any platform or language should[…]
-
Re: iTWire - Transport for NSW and HCLTech expand digital transformation partnership
Ajai Chowdhry, one of the founders and CEO of HCL is married to a cousin of a cousin of mine.[…]
-
Re: iTWire - NBN Co demonstrates fibre-like speeds over HFC network in trial
I wonder when they will implement all of this, and what the pricing plans will be.FWIW, these days the proposed[…]





































