Displaying items by tag: Outlook
How to Repair Corrupt Outlook Data File (PST)?
Personal Storage Table or PST is a popular and most commonly used mailbox data file format for storing, backing up, and migrating mail items to and from Microsoft Outlook.
Vodafone harnesses Microsoft AI for its employees
Microsoft announced it will provide Microsoft 365 Copilot AI software for up to 68,000 Vodafone employees across multiple countries.
KnowBe4 Collaborates With Microsoft on the New Microsoft Ribbon Phish Alert Button
New Microsoft Ribbon Phish Alert Button (PAB) by KnowBe4 to enhance email security for Outlook users globally
How To Get MS Outlook Data Repaired From a Vvew Virus Attack
Several people lose their Microsoft Outlook data because of Vvew virus attacks. Many people are unaware of the solutions to this problem and ultimately lose important information. At the same time, this is all they need to recover their files.
It is essential to note that the Vvew virus is an Avant virus that attacks computers through emails and website pages. It has layered blocks of designs used to attack, encode, and erase MS Outlook PST files. Once it strikes any .PST file, it alters its code and changes its extension to .vvew. Once this happens, you cannot use your Outlook files or mail because your MS Outlook reads files with .PST and OST extensions.
While the Vvew virus might seem harmful to files and data, the Recovery Toolbox for Outlook has powerful algorithms to scan every file from the email box and repair it. There are two methods to solve the problem with this tool. They are:
- The online method: https://outlook.recoverytoolbox.com/online/
- The offline method: https://outlook.recoverytoolbox.com/repair-outlook/
The two methods are workable to solve the virus attack because the tool has an online and offline version. You can use these versions to recover encrypted .PST files (.PST across all versions– ANSI (Outlook 97-2003), Unicode (2007 and above)).
Read through to understand how to recover and restore your Microsoft Outlook files.
The Online Method: How to Recover Your PST File with Recovery Toolbox for Outlook
You can easily use this to regain your affected information online. This recovery process works effectively on all devices as smoothly and swiftly as possible to restore OST files and fix your encrypted .PST files.
Follow these steps to repair your files online:
- You must change the file extension from Vvew to PST for the service to select the recovery algorithm to use.
- Click “Select file” and select an Outlook data file with the extension “.PST” or “.OST.”
- Input your valid email address
- Click Continue
- Wait for the corrupted .pst/.ost file to be recovered
- Download the recovered Microsoft Outlook pst file
Once you have recovered the data from the affected MS Outlook file, it will be stored as a new MS Outlook 2016 file with the .PST extension. This way, it will be easy to regain any .PST MS Outlook private file through any browser and device.
The Offline Method: How to Recover Your Infected .PST with Recovery Toolbox for Outlook
Before you begin, you must look for your Outlook Data Files in Outlook before repairing infected .pst files. Follow these steps
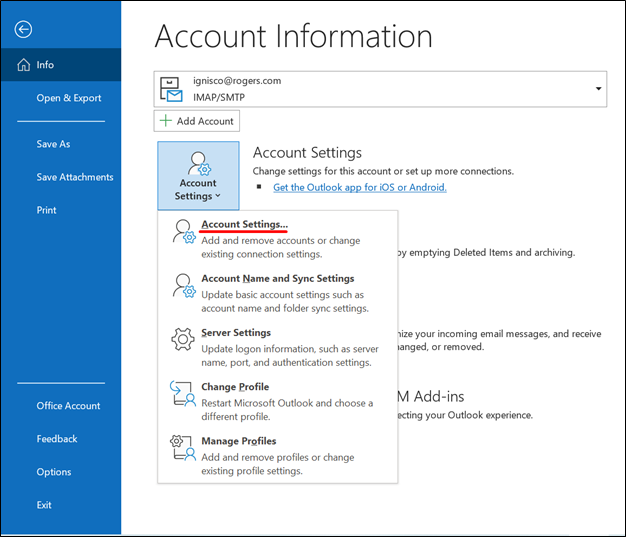
- First, select File, Choose Account Settings, and Click Account Settings.
- Next, select the Data Files
- You will see all Outlook Data Files (.PST) and Offline Data Files (.OST) listed, along with the account name the files are associated with.
Once you have been able to locate all your Outlook files, take these steps to repair your attacked file.
Step 1. Identify the infected Outlook data file location
To recover an infected Outlook data file, first Exit Microsoft Outlook and check one of these locations:
- For Outlook 365: C:\Users\Username\AppData\Local\Microsoft\Outlook\
- For Outlook 2019: C:\Documents and Settings\user\Local Settings\Application Data\Microsoft\Outlook
- For Outlook 2016: C:\Documents and Settings\user\Local Settings\Application Data\Microsoft\Outlook
- For Outlook 2013: C:\Documents and Settings\user\Local Settings\Application Data\Microsoft\Outlook
- For Outlook 2010: C:\Documents and Settings\user\Local Settings\Application Data\Microsoft\Outlook
- For Outlook 2007: C:\Documents and Settings\user\Local Settings\Application Data\Microsoft\Outlook
- For Outlook 2003: C:\Users\username\Documents\Outlook Files\
- For Outlook XP: C:\Documents and Settings\Username\Local Settings\Application Data\Microsoft\Outlook
- For Outlook 2000: C:\Documents and Settings\Username\Local Settings\Application Data\Microsoft\Outlook
Step 2: Download, install the program and Run it.
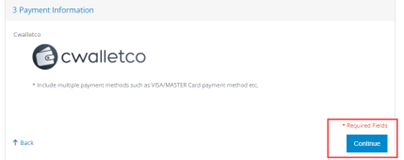
Step 3: Choose the file encrypted by the virus and select Next.
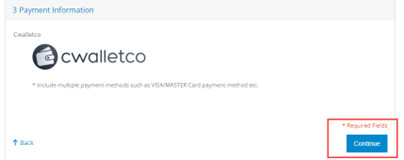
Step 4: Select Recovery Mode and Click Next.
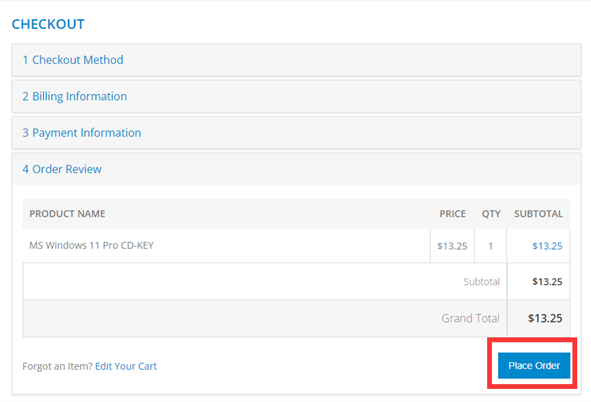
Step 5: Click on Yes to begin recovery.
Step 6: Inspect the data preview and click Next to save the recovered file to a new location.
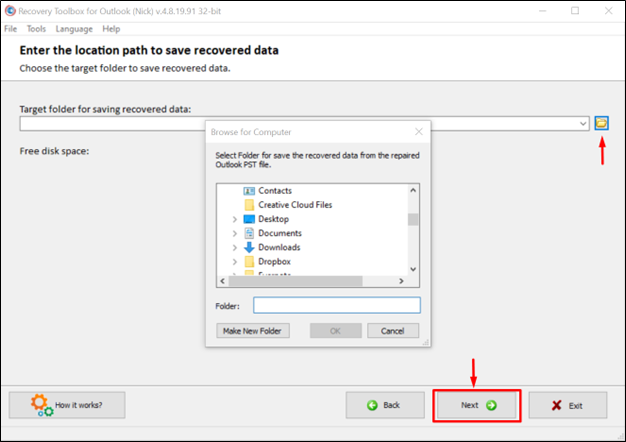
Step 7: Enter the location to save the .pst file and click Next.
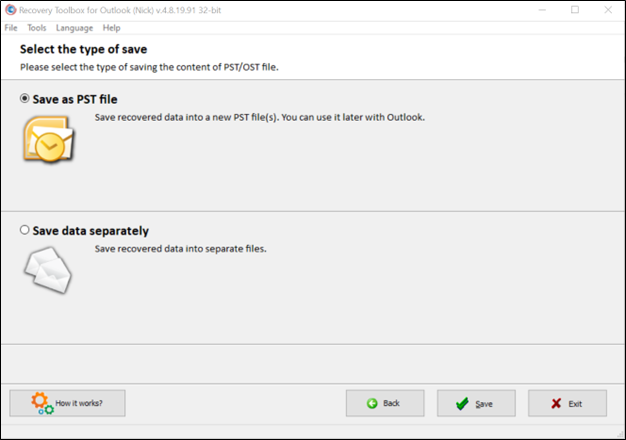
Step 8: Save the recovered data as the new .pst file.
Step 9: After checking the successful recovery results, click Finish to exit the Recovery Toolbox for Outlook tool.
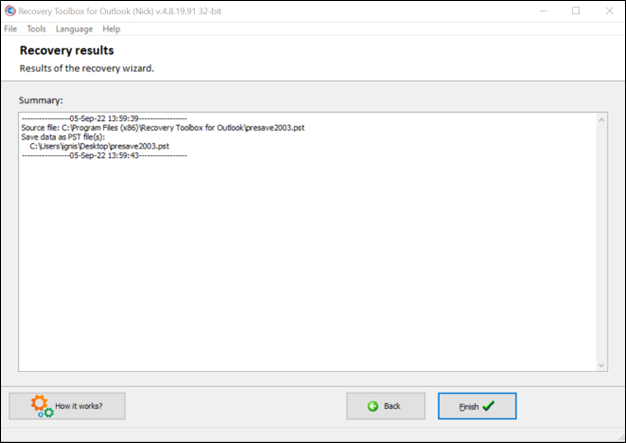
It is important to note that you should substitute the damaged file with a recovered one. You can also add the recovered .pst file to the list of data files in Outlook. This is how you do it for these versions of Outlook: 2021, 2019, 2016, and 2013:
- Choose the menu item File | Info.
- Next, click the button Account Settings.
- Finally, choose Account Settings in the pop-up menu.
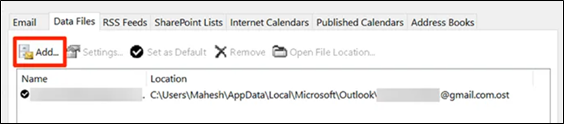
- Choose the Data Files tab and click Remove.
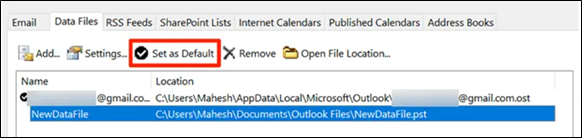
- Click Open File Location and select the recovered file. Click Set as Default.
Once you have reached this stage, you have successfully fixed the issue.
Conclusion
The Recovery Toolbox for Outlook uses high-grade algorithms and procedures in analyzing, fixing, and restoring files, irrespective of the problem or its cause– i.e., viruses, bugs, hardware damage, network problems, HDD damage, etc.
The tool has the following advantages:
- With the tool, you can fix Microsoft Outlook files with .PST extension across different versions (ANSI (Outlook 97-2003), Unicode (2007 and above)).
- The recovery tool allows you to repair and recover files protected by a password.
- With the tool, you can recover damaged (or attacked) OST files irrespective of their versions.
- The tool allows you to repair encrypted files with the .PST extension.
- You can quickly repair PST files of different sizes, up to 180 Gigabytes, and more.
The Recovery Toolbox for Outlook is very efficient for repairing and recovering every kind of file and data on Microsoft Outlook. You can use it to easily access damaged, password-protected, and encrypted files like contacts, tasks, documents, etc. The tool is easy to use and is effective both online and offline.
NodeStealer attacks on Facebook take a ‘provocative turn’ – threat actors deploy malvertising campaigns to ‘hijack users’ accounts: Bitdefender
Cybersecurity solutions provider Bitdefender Labs says it has been monitoring the growing trend among cybercriminals who actively exploit social media networks for malvertising, and the “end goal of these attacks” is to hijack accounts and “steal personal data” through malicious software.
Microsoft cloud breach report 'leaves many questions unanswered'
Cloud security company Wiz.io says there are many unanswered questions raised by Microsoft's final report into a breach of its Azure cloud platform, pointing out that the threat actor, given the name Storm-0558, may have been forging authentication tokens for more than two years given the timeline in the report.
Microsoft August Patch Tuesday sees less fixes in the pipeline
Microsoft has released patches for 73 CVEs as part of its monthly Patch Tuesday fixes, including one for a vulnerability that is being exploited in the wild.
Azure breach: Microsoft okays Wiz post on continued danger, then denies it
Microsoft is continuing to obfuscate about a recent attack on its Azure cloud infrastructure, saying a post, that claims danger from the attack still exists, is speculative and not evidence-based.
Microsoft comes under pressure as more details of breach emerge
Microsoft is coming under increasing pressure from both the security community and the US Government after it was disclosed that the company's cloud platform was breached and emails stolen from a number of government agencies, allegedly by Chinese attackers.
Microsoft claims Azure, Outlook June outages due to DDoS attacks
Software giant Microsoft claims outages to its Outlook, OneDrive and Azure services earlier this month were due to distributed denial of service attacks staged by a group it calls Storm-1359.
Microsoft looks to extend its tentacles further into Pentagon networks
Microsoft releases 80 patches, including two for exploited zero-days
Microsoft has warned users of two zero-day vulnerabilities that have been exploited as it issued a total of 80 patches on its monthly Patch Tuesday.
Google blames Microsoft 'monoculture' for govt security problems
Google has taken a potshot at Microsoft, something it does occasionally, using a survey conducted by Public Opinion Strategies — and paid for by its own cloud business — to ventilate the concerns of government users who are mostly locked into a Microsoft environment.
Tech experts share their five top data migration tips
GUEST OPINION: An absolute must for all organisations planning a data migration, however complex, is to research vendors whose technology can simplify the migration – and choose the one with the most comprehensive solution and top support.
iTWireTV Interview: Barco A/NZ MD, Claudio Cardile, shares a fresh outlook for the post-Covid workplace
GUEST INTERVIEW: Although the spectre of Omicron hovers, people are nevertheless returning to work in a hybrid fashion, with the demand for modern, fast and fluid videoconferencing experiences never greater, whether at home, at work, or other remote working scenarios, so what are the trends for a world on the mend?
VIDEO Interview: Barco A/NZ MD, Claudio Cardile, shares a fresh outlook for the post-Covid workplace
GUEST INTERVIEW: Although the spectre of Omicron hovers, people are nevertheless returning to work in a hybrid fashion, with the demand for modern, fast and fluid videoconferencing experiences never greater, whether at home, at work, or other remote working scenarios, so what are the trends for a world on the mend?
Sec firm defends release of Exchange flaw details without telling Microsoft
A researcher at a security firm that disclosed an issue with a protocol in the Microsoft Exchange mail server software has defended not having made contact with the company before releasing his findings, saying the issue had been known for seven years.
Microsoft Exchange leaking user credentials due to protocol defect
A protocol used by Microsoft Exchange, the popular email server software used by both individuals and businesses, has been found to be leaking credentials of users, who attempt to authenticate from clients like Microsoft Outlook, due to a defect in its design.
Microsoft offers passwordless feature to users
Passwords are inconvenient, and they’re prime target for attacks. For years, they’ve been the most important layer of security in the digital realm—from email to bank accounts, shopping carts to video games.
Aussie Broadband announces 'bloody good' half year results to 31 Dec 2020
Aussie Broadband is the company that offers "bloody good broadband", so when we looked at its half year results, we thought they were bloody good, too!
WEBINARS & EVENTS
- UiPath to Unveil Latest Agentic Automation Solutions at Agentic AI Summit
- ALL WELCOME - 6 DAYS TO GO - AI in Action is your opportunity to gain actionable strategies for deploying scalable, reliable AI solutions that drive measurable business outcomes.
- TODAY FREE VIRTUAL EVENT - EXL SERVICE, AI in action Driving the shift to scalable AI
- Expert warns: Small businesses missing out on AI cost-saving and growth opportunities
- Datadog Opens Registration for Its 2025 DASH Conference
CYBERSECURITY
- Nozomi Networks Named to Fast Company’s World’s Most Innovative Companies 2025 List
- Cybersecurity for Small and Medium Businesses in 2025: Challenges and Solutions
- New initiatives to combat SMS scams and build confidence in Australian phone numbers and brands
- Milestone Systems Expands XProtect with Enhanced CLOUD Integration, Advanced Vehicle Analytics
- Fastly Empowers Organisations to Prioritise Security Without Disrupting End-User Experiences
PEOPLE MOVES
- DataSnipper appoints Siu Wei Lee to lead Asia Pacific expansion
- Zetaris, The Modern Lakehouse for AI, Continues its Global Expansion with Appointment of Robert Herjavec as Executive Director Global Strategy
- Wisr Welcomes Inaugural Chief Innovation Officer
- Rubrik Welcomes Sathish Murthy as the Company’s New Field CTO, APJ
- Seeing Machines appoints John Noble as technology chief
GUEST ARTICLES
- Unlock online freedom with a free VPN
- AI and the Future of Insurance: Why Solving the Data Integration Challenge Matters
- What are haplogroups, and how do they connect with ethnicity?
- Why Missouri car accident victims should act fast to protect their legal rights
- What to bring to your first meeting with a Florida personal injury lawyer
- TELETRAC NAVMAN survey finds 83% of fleets say that AI is future of safety
- Workplace Tug-of-War: Organisations Mandate Office Days, But Employees Push for More Flexibility
-
How to prevent tool wear and damage in CNC Aluminum Processing
GUEST OPINION: In the world of precision manufacturing, maintaining the…
- New Trustwave research finds patient lives at risk in healthcare with cybersecurity vulnerabilities
- Anti Scam Investment Much Needed
Guest Opinion
- Unlock online freedom with a free VPN
- AI and the Future of Insurance: Why Solving the Data Integration Challenge Matters
- What are haplogroups, and how do they connect with ethnicity?
- Why Missouri car accident victims should act fast to protect their legal rights
- What to bring to your first meeting with a Florida personal injury lawyer
-
How to prevent tool wear and damage in CNC Aluminum Processing
GUEST OPINION: In the world of precision manufacturing, maintaining the…
- Anti Scam Investment Much Needed
- Govt must Incentivise People Initiatives to Beat Productivity Slump
- Network Technologies Driving Sustainability for Education and Hospitality in 2025
- Transitioning to a new ERP system is like open heart surgery for business
ITWIRETV & INTERVIEWS
- Amazon CISO CJ Moses gives rare interview
- Matt Salier explains the Australian Cyber Collaboration Centre's voluntary data classification framework
- Qualys CEO Sumedh Thakar explains the Risk Operations Centre (ROC)
- iTWire talks to SailPoint about identity management in the Enterprise
- How Blue Yonder is applying AI and innovation to solve supply chain challenges
RESEARCH & CASE STUDIES
Channel News
Comments
-
Re: iTWire - Why Software Developers Need a Security ‘Rewards Program’
For most developers the security/performance trade off is still the hardest one to tackle, even as the cost of processing[…]
-
Re: iTWire - The Risc-V architecture that can shape the future of computing
RISC has been overhyped. While it is an interesting low-level processor architecture, what the world needs is high-level system architectures,[…]
-
Re: iTWire - Is Linux finally ready to storm the mainstream?
There are two flaws that are widespread in the industry here. The first is that any platform or language should[…]
-
Re: iTWire - Transport for NSW and HCLTech expand digital transformation partnership
Ajai Chowdhry, one of the founders and CEO of HCL is married to a cousin of a cousin of mine.[…]
-
Re: iTWire - NBN Co demonstrates fibre-like speeds over HFC network in trial
I wonder when they will implement all of this, and what the pricing plans will be.FWIW, these days the proposed[…]




































