Displaying items by tag: recovery
Commvault and SimSpace Revolutionise Cyber Resilience with Real-World Recovery Training
In a groundbreaking move to redefine cyber resilience, Commvault and SimSpace have unveiled the Commvault Recovery Range, a first-of-its-kind cyber range that seamlessly integrates real-world attack simulations with end-to-end recovery exercises. This pioneering solution empowers security professionals to experience, respond to, and recover from sophisticated cyberattacks in a high-fidelity environment that mirrors actual production systems.
Semperis World Backup Day
The celebration of the 15th anniversary of World Backup Day serves as a reminder for individuals and businesses to reflect on their data protection strategies and ensure their data is adequately safeguarded. Quality backup is the linchpin of business resilience, shielding against data loss and ransomware threats, and ensuring swift recovery in the face of unforeseen challenges.
Commvault Partners with CrowdStrike to Accelerate Threat Detection and Safe Recovery
Commvault delivers new integration with the CrowdStrike Falcon platform to help joint customers improve cyber readiness and achieve continuous business.
Commvault Automates Active Directory Forest Recovery to Protect 'Keys to the Kingdom' Amidst Rampant and Debilitating Ransomware Attacks
Leverages the same platform that already delivers comprehensive protection of critical workloads – ushering in a new level of cyber resilience for customers and partners
Rubrik Debuts Turbo Threat Hunting
- Internal test shows estimated scanning speeds of 75,000 backups within 60 seconds
- Designed to enable organisations to identify clean recovery points in seconds, minimising downtime after cyberattacks
Safeguard Critical Microsoft 365 Data With Office 365 Backup and Recovery Solution
Microsoft 365 Suite is widely used, offering a range of applications to meet various needs. Protecting the data within Office 365 applications is important, and businesses need a robust backup plan to safeguard critical data against accidental data deletion, security threats, and ensure business continuity and compliance.
How To Get MS Outlook Data Repaired From a Vvew Virus Attack
Several people lose their Microsoft Outlook data because of Vvew virus attacks. Many people are unaware of the solutions to this problem and ultimately lose important information. At the same time, this is all they need to recover their files.
It is essential to note that the Vvew virus is an Avant virus that attacks computers through emails and website pages. It has layered blocks of designs used to attack, encode, and erase MS Outlook PST files. Once it strikes any .PST file, it alters its code and changes its extension to .vvew. Once this happens, you cannot use your Outlook files or mail because your MS Outlook reads files with .PST and OST extensions.
While the Vvew virus might seem harmful to files and data, the Recovery Toolbox for Outlook has powerful algorithms to scan every file from the email box and repair it. There are two methods to solve the problem with this tool. They are:
- The online method: https://outlook.recoverytoolbox.com/online/
- The offline method: https://outlook.recoverytoolbox.com/repair-outlook/
The two methods are workable to solve the virus attack because the tool has an online and offline version. You can use these versions to recover encrypted .PST files (.PST across all versions– ANSI (Outlook 97-2003), Unicode (2007 and above)).
Read through to understand how to recover and restore your Microsoft Outlook files.
The Online Method: How to Recover Your PST File with Recovery Toolbox for Outlook
You can easily use this to regain your affected information online. This recovery process works effectively on all devices as smoothly and swiftly as possible to restore OST files and fix your encrypted .PST files.
Follow these steps to repair your files online:
- You must change the file extension from Vvew to PST for the service to select the recovery algorithm to use.
- Click “Select file” and select an Outlook data file with the extension “.PST” or “.OST.”
- Input your valid email address
- Click Continue
- Wait for the corrupted .pst/.ost file to be recovered
- Download the recovered Microsoft Outlook pst file
Once you have recovered the data from the affected MS Outlook file, it will be stored as a new MS Outlook 2016 file with the .PST extension. This way, it will be easy to regain any .PST MS Outlook private file through any browser and device.
The Offline Method: How to Recover Your Infected .PST with Recovery Toolbox for Outlook
Before you begin, you must look for your Outlook Data Files in Outlook before repairing infected .pst files. Follow these steps
- First, select File, Choose Account Settings, and Click Account Settings.
- Next, select the Data Files
- You will see all Outlook Data Files (.PST) and Offline Data Files (.OST) listed, along with the account name the files are associated with.
Once you have been able to locate all your Outlook files, take these steps to repair your attacked file.
Step 1. Identify the infected Outlook data file location
To recover an infected Outlook data file, first Exit Microsoft Outlook and check one of these locations:
- For Outlook 365: C:\Users\Username\AppData\Local\Microsoft\Outlook\
- For Outlook 2019: C:\Documents and Settings\user\Local Settings\Application Data\Microsoft\Outlook
- For Outlook 2016: C:\Documents and Settings\user\Local Settings\Application Data\Microsoft\Outlook
- For Outlook 2013: C:\Documents and Settings\user\Local Settings\Application Data\Microsoft\Outlook
- For Outlook 2010: C:\Documents and Settings\user\Local Settings\Application Data\Microsoft\Outlook
- For Outlook 2007: C:\Documents and Settings\user\Local Settings\Application Data\Microsoft\Outlook
- For Outlook 2003: C:\Users\username\Documents\Outlook Files\
- For Outlook XP: C:\Documents and Settings\Username\Local Settings\Application Data\Microsoft\Outlook
- For Outlook 2000: C:\Documents and Settings\Username\Local Settings\Application Data\Microsoft\Outlook
Step 2: Download, install the program and Run it.
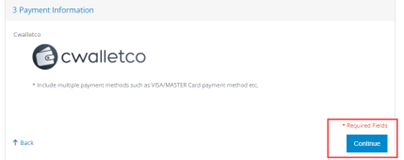
Step 3: Choose the file encrypted by the virus and select Next.
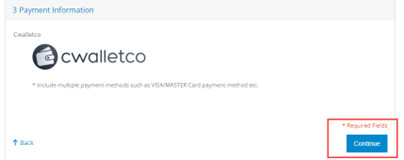
Step 4: Select Recovery Mode and Click Next.
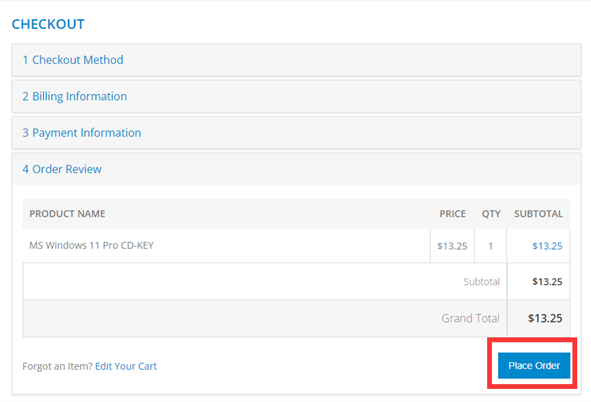
Step 5: Click on Yes to begin recovery.
Step 6: Inspect the data preview and click Next to save the recovered file to a new location.
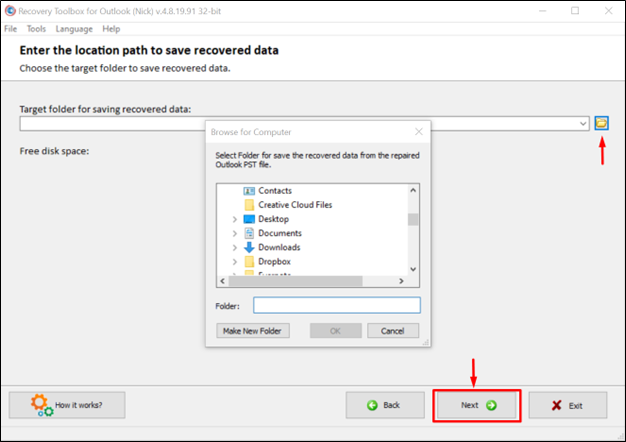
Step 7: Enter the location to save the .pst file and click Next.
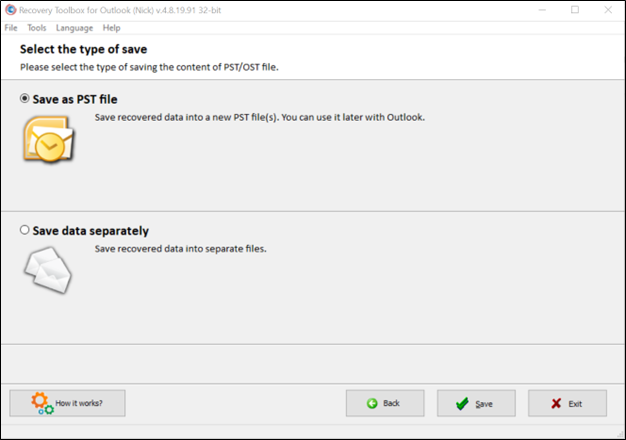
Step 8: Save the recovered data as the new .pst file.
Step 9: After checking the successful recovery results, click Finish to exit the Recovery Toolbox for Outlook tool.
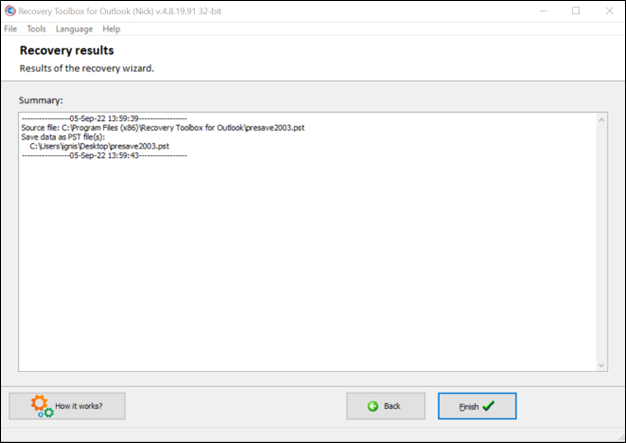
It is important to note that you should substitute the damaged file with a recovered one. You can also add the recovered .pst file to the list of data files in Outlook. This is how you do it for these versions of Outlook: 2021, 2019, 2016, and 2013:
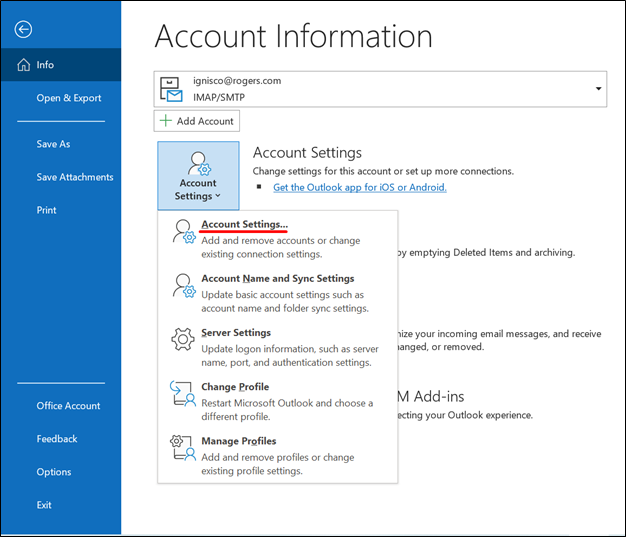
- Choose the menu item File | Info.
- Next, click the button Account Settings.
- Finally, choose Account Settings in the pop-up menu.
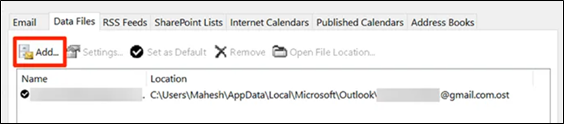
- Choose the Data Files tab and click Remove.
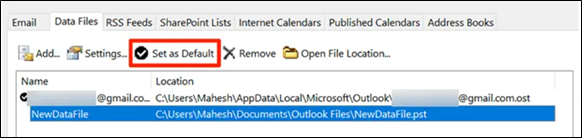
- Click Open File Location and select the recovered file. Click Set as Default.
Once you have reached this stage, you have successfully fixed the issue.
Conclusion
The Recovery Toolbox for Outlook uses high-grade algorithms and procedures in analyzing, fixing, and restoring files, irrespective of the problem or its cause– i.e., viruses, bugs, hardware damage, network problems, HDD damage, etc.
The tool has the following advantages:
- With the tool, you can fix Microsoft Outlook files with .PST extension across different versions (ANSI (Outlook 97-2003), Unicode (2007 and above)).
- The recovery tool allows you to repair and recover files protected by a password.
- With the tool, you can recover damaged (or attacked) OST files irrespective of their versions.
- The tool allows you to repair encrypted files with the .PST extension.
- You can quickly repair PST files of different sizes, up to 180 Gigabytes, and more.
The Recovery Toolbox for Outlook is very efficient for repairing and recovering every kind of file and data on Microsoft Outlook. You can use it to easily access damaged, password-protected, and encrypted files like contacts, tasks, documents, etc. The tool is easy to use and is effective both online and offline.
Rubrik Named a Leader in IDC MarketScape for Worldwide Cyber Recovery
GUEST RESEARCH: Data security provider recognised for strengths in extensive cybersecurity posture capabilities

A Look into Stellar Repair for Outlook an Advanced PST Repair tool
PROMOTION Stellar Repair for Outlook is an innovative and advanced software, intended to repair damaged or corrupted PST files. This software can restore all the mail items, including emails, attachments, contacts, calendars, tasks, and journals, from corrupted PST files. It can also retrieve deleted emails and display a preview of all the recoverable data before saving. With numerous advanced features and simplicity of use, it is one of the best software for PST file repair and recovery.
The key to cyberattack recovery is resilience, and the key to resilience is hiding in your BIOS all along
Fending off cyberattacks is a relentless battle. Businesses must allocate resources toward building resilience, says Absolute Software CTO Nicko van Someren. And he should know; his company's software is embedded in almost every laptop shipped in the last 15 years.
Rubrik announces AI-supported cyber recovery for VMware environments
Security specialist Rubrik's new Rubrik AI-Powered Cyber Recovery provides generative AI capabilities for VMware customers to help minimise data loss and reduce downtime following a cyberattack.
Synology releases the effortless BeeDrive personal backup system
Storage and networking hardware provider Synology has released its new BeeDrive, a tiny data hub that backs up personal files and photos from your computer, phone, and tablet simultaneously, with an extremely simple setup.
Therabody, makers of the original Theragun, has a limited-time sale
Although it is possible to buy clones of Therabody's Theragun devices at various stores and online, Therabody's introduction of the Theragun in 2008 set off a persuasive massage therapy revolution that still reverberates to this day, and you can buy one of the models from up to $240 off.
iTWireTV Interview: Barco A/NZ MD, Claudio Cardile, shares a fresh outlook for the post-Covid workplace
GUEST INTERVIEW: Although the spectre of Omicron hovers, people are nevertheless returning to work in a hybrid fashion, with the demand for modern, fast and fluid videoconferencing experiences never greater, whether at home, at work, or other remote working scenarios, so what are the trends for a world on the mend?
VIDEO Interview: Barco A/NZ MD, Claudio Cardile, shares a fresh outlook for the post-Covid workplace
GUEST INTERVIEW: Although the spectre of Omicron hovers, people are nevertheless returning to work in a hybrid fashion, with the demand for modern, fast and fluid videoconferencing experiences never greater, whether at home, at work, or other remote working scenarios, so what are the trends for a world on the mend?
Blackberry delivers Alert critical event management solution
Security software and services firm Blackberry has announced a new critical event management (CEM) solution - BlackBerry Alert - designed to help commercial organisations prepare for, respond to and recover from major incidents.
VIDEO Interview: Key retail post-COVID insights revealed by Zebra's 2021 shopper study; March 17 Webinar Invite
Zebra's A/NZ director, Tom Christodoulou, and Daniel Park, Sales Engineer Manager, reveal in an exclusive video interview, what customers want in a post-COVID world, leading to retailers quickly adapting to an on-demand reality augmented by enterprise-grade technology delivering connectivity, productivity and customer satisfaction as never before.
VIDEO Interview: Key retail post-COVID insights revealed by Zebra's 2021 shopper study; March 17 Webinar Invite
Zebra's A/NZ director, Tom Christodoulou, and Daniel Park, Sales Engineer Manager, reveal in an exclusive video interview, what customers want in a post-COVID world, leading to retailers quickly adapting to an on-demand reality augmented by enterprise-grade technology delivering connectivity, productivity and customer satisfaction as never before.
The silent but critical foundation needed to support regional prosperity
GUEST OPINION by Brett Barningham, Managing Director of Local and State Government ANZ, Civica. The government’s latest Budget has been described by some as one of “shock and awe” levels of spending, including billions on regional infrastructure. The figures are truly eye-watering – and confirmation that the government is seeking to use its purchasing power to enhance overall demand amid a record recession.
Businesses must plan COVID-19 recovery now, says analyst
Businesses must start planning their recoveries now from the COVID 19 pandemic crisis to avoid devastating long-term financial impacts, despite the fact that the businesses are still grappling with daily disruptions as the pandemic continues to increase, according to one global analyst firm.
WEBINARS & EVENTS
- OutSystems Announces ONE 2025: The Future of AI-Powered Application and Agent Development Unveiled
- 8 DAYS TO GO - Maximising Cloud Efficiency - How to do more with Less
- 12 DAYS TO GO - Maximising Cloud Efficiency - How to do more with Less
- UiPath to Unveil Latest Agentic Automation Solutions at Agentic AI Summit
- ALL WELCOME - 6 DAYS TO GO - AI in Action is your opportunity to gain actionable strategies for deploying scalable, reliable AI solutions that drive measurable business outcomes.
CYBERSECURITY
- Australians warned: 'Election scams on the rise' following U.S. Trends
- The Blue Team Burnout and How to Prevent It
- Report reveals record-breaking year for Microsoft vulnerabilities
- SentinelOne Recognised as the Best Performing Vendor in Frost Radar Endpoint Security, 2025
- Introducing Illumio Insights: AI Cloud Detection and Response
PEOPLE MOVES
- Barracuda Appoints Ketan Tailor as Chief Customer Officer
- SYSPRO appoints Leanne Taylor as Chief Revenue Officer
- Cloudian appoints new APJ Channel and Marketing Directors
- Salus Ventures welcomes Defence Industry Veteran Dr Shane Arnott as Senior Advisor
- Ericsson appoints new Head of Australia and New Zealand
GUEST ARTICLES
- OutSystems Announces ONE 2025: The Future of AI-Powered Application and Agent Development Unveiled
- National 'research and development crisis' calling for Team Australia
- AI Hype Cycle meets Reality for Construction Industry
- New Book from Boomi Warns: AI Will Fail Without a Digital Infrastructure Overhaul
- Research Firm Names Datadog an AIOps Market Leader
- Why finance teams can’t afford to ignore shifting spend trends and artificial intelligence innovation
-
Why I switched from AliExpress to local suppliers for Amazon dropshipping
GUEST OPINION: My dropshipping journey with Amazon began like most…
-
How social media automation can boost your sales
GUEST OPINION: Social media isn’t just for brand awareness anymore.…
Guest Opinion
- New Book from Boomi Warns: AI Will Fail Without a Digital Infrastructure Overhaul
- Why finance teams can’t afford to ignore shifting spend trends and artificial intelligence innovation
-
Why I switched from AliExpress to local suppliers for Amazon dropshipping
GUEST OPINION: My dropshipping journey with Amazon began like most…
-
How social media automation can boost your sales
GUEST OPINION: Social media isn’t just for brand awareness anymore.…
-
5 Secrets to Faster Innovation in IT You Can't Avoid to Ignore
GUEST OPINION: Imagine this scenario: Two competing financial institutions decide…
-
This is why great content alone won’t get you found on Google
GUEST OPINION: You just dropped what you know is a…
- Why Limiting Your Hiring to One Country Is Holding Your Business Back
- Data Management – It’s a High-Stakes Game
ITWIRETV & INTERVIEWS
- Amazon CISO CJ Moses gives rare interview
- Matt Salier explains the Australian Cyber Collaboration Centre's voluntary data classification framework
- Qualys CEO Sumedh Thakar explains the Risk Operations Centre (ROC)
- iTWire talks to SailPoint about identity management in the Enterprise
- How Blue Yonder is applying AI and innovation to solve supply chain challenges
RESEARCH & CASE STUDIES
Channel News
Comments
-
Re: iTWire - Can cyber security be a platform for innovation and growth?
Most cybersecurity is making up for weak platforms. We need to address the fundamentals, design platforms that prevent out-of-bounds access[…]
-
Re: iTWire - Why Software Developers Need a Security ‘Rewards Program’
For most developers the security/performance trade off is still the hardest one to tackle, even as the cost of processing[…]
-
Re: iTWire - The Risc-V architecture that can shape the future of computing
RISC has been overhyped. While it is an interesting low-level processor architecture, what the world needs is high-level system architectures,[…]
-
Re: iTWire - Is Linux finally ready to storm the mainstream?
There are two flaws that are widespread in the industry here. The first is that any platform or language should[…]
-
Re: iTWire - Transport for NSW and HCLTech expand digital transformation partnership
Ajai Chowdhry, one of the founders and CEO of HCL is married to a cousin of a cousin of mine.[…]































