Displaying items by tag: Attack
Self-Inflicted Cloud Wounds Still the Top risk in Cloud Security, New Report Finds
GUEST RESEARCH: Qualys has released The State of Cloud & SaaS Security Report. The survey, commissioned by Qualys and conducted by Dark Reading reveals that human error remains the most prevalent cloud and SaaS security risk, despite the growing sophistication of attacker tactics.
Deep observability. Having a moment in 2025
When the Australian National University experienced a data breach a few years ago, it was a big wake up call.
Semperis World Backup Day
The celebration of the 15th anniversary of World Backup Day serves as a reminder for individuals and businesses to reflect on their data protection strategies and ensure their data is adequately safeguarded. Quality backup is the linchpin of business resilience, shielding against data loss and ransomware threats, and ensuring swift recovery in the face of unforeseen challenges.
Netflix’s Zero Day is a Half-Truth About Cyber Warfare
GUEST OPINION: Netflix’s Zero Day delivers a gripping cyber thriller, dramatising a large-scale attack on U.S. critical infrastructure. It’s suspenseful, and packed with high-level political intrigue, but like any Hollywood production, it bends the truth to fit the narrative. Robert De Niro’s character, former President Mullen, makes a statement early in the pilot that feels eerily close to reality:
F5 equips network and security teams with AI assistant for F5 Distributed Cloud Services
- ‘Intelligent partner’ for SecOps and NetOps will allow teams to query network activity, drill down into security events and rapidly implement mitigations
- New support for teams who must manage more deployment models than ever, with 88% of organisations now employing a hybrid approach
The Overlooked Essentials in Cybersecurity Preparedness
While organizations pour resources into advanced threat detection systems and cutting-edge security tools, they often miss fundamental elements that could make or break their cybersecurity defenses. These overlooked components create vulnerabilities that sophisticated attackers are all too happy to exploit.
2024 Threat Landscape: Ransomware Activity, Vulnerability Exploits, and Attack Trends
GUEST OPINION: Now we’ve reached the end of another year, you may be looking around the cybersecurity infosphere and seeing a glut of posts offering “hot takes” on the 2024 threat landscape and predictions about what’s coming next. At Rapid7, we don’t truck in hot takes, but rather, cold hard facts. Staying ahead of adversaries requires more than just advanced tools; it requires the latest intelligence and collaborative insights from experts working from data that tells the whole story.
Cyberthreat Predictions for 2025 from Barracuda’s Security Frontline
GUEST OPINION: Predicting the future isn’t easy, but you can anticipate what is likely to happen by looking at how things have evolved over the past year. This year again, Barracuda asked colleagues who work on the security frontlines about the things they witnessed in 2024 and expect to see in 2025.
The Dark Side of Domain-Specific Languages: Tenable Uncovers New Attack Techniques in Open Source Software
Tenable, the exposure management company, has disclosed that its Tenable Cloud Security Research team has uncovered new attack techniques in Domain-Specific Languages (DSLs) of popular policy-as-code (PaC) and infrastructure-as-code (IaC) platforms. These can lead to compromised cloud identities, lateral movement, and data exfiltration.
Unmanaged Devices: A Critical Cybersecurity Concern for CISOs
Throughout human history, there have been many instances where the number 3 has had a unique significance. In ancient Greece, for example, it was considered the perfect number reflecting harmony, wisdom and understanding. For me, I find that if three or more unrelated people start talking about a specific topic, it takes on a particular relevance. The topic of the moment on every CISO’s lips seems to be unmanaged devices.
How To Get MS Outlook Data Repaired From a Vvew Virus Attack
Several people lose their Microsoft Outlook data because of Vvew virus attacks. Many people are unaware of the solutions to this problem and ultimately lose important information. At the same time, this is all they need to recover their files.
It is essential to note that the Vvew virus is an Avant virus that attacks computers through emails and website pages. It has layered blocks of designs used to attack, encode, and erase MS Outlook PST files. Once it strikes any .PST file, it alters its code and changes its extension to .vvew. Once this happens, you cannot use your Outlook files or mail because your MS Outlook reads files with .PST and OST extensions.
While the Vvew virus might seem harmful to files and data, the Recovery Toolbox for Outlook has powerful algorithms to scan every file from the email box and repair it. There are two methods to solve the problem with this tool. They are:
- The online method: https://outlook.recoverytoolbox.com/online/
- The offline method: https://outlook.recoverytoolbox.com/repair-outlook/
The two methods are workable to solve the virus attack because the tool has an online and offline version. You can use these versions to recover encrypted .PST files (.PST across all versions– ANSI (Outlook 97-2003), Unicode (2007 and above)).
Read through to understand how to recover and restore your Microsoft Outlook files.
The Online Method: How to Recover Your PST File with Recovery Toolbox for Outlook
You can easily use this to regain your affected information online. This recovery process works effectively on all devices as smoothly and swiftly as possible to restore OST files and fix your encrypted .PST files.
Follow these steps to repair your files online:
- You must change the file extension from Vvew to PST for the service to select the recovery algorithm to use.
- Click “Select file” and select an Outlook data file with the extension “.PST” or “.OST.”
- Input your valid email address
- Click Continue
- Wait for the corrupted .pst/.ost file to be recovered
- Download the recovered Microsoft Outlook pst file
Once you have recovered the data from the affected MS Outlook file, it will be stored as a new MS Outlook 2016 file with the .PST extension. This way, it will be easy to regain any .PST MS Outlook private file through any browser and device.
The Offline Method: How to Recover Your Infected .PST with Recovery Toolbox for Outlook
Before you begin, you must look for your Outlook Data Files in Outlook before repairing infected .pst files. Follow these steps
- First, select File, Choose Account Settings, and Click Account Settings.
- Next, select the Data Files
- You will see all Outlook Data Files (.PST) and Offline Data Files (.OST) listed, along with the account name the files are associated with.
Once you have been able to locate all your Outlook files, take these steps to repair your attacked file.
Step 1. Identify the infected Outlook data file location
To recover an infected Outlook data file, first Exit Microsoft Outlook and check one of these locations:
- For Outlook 365: C:\Users\Username\AppData\Local\Microsoft\Outlook\
- For Outlook 2019: C:\Documents and Settings\user\Local Settings\Application Data\Microsoft\Outlook
- For Outlook 2016: C:\Documents and Settings\user\Local Settings\Application Data\Microsoft\Outlook
- For Outlook 2013: C:\Documents and Settings\user\Local Settings\Application Data\Microsoft\Outlook
- For Outlook 2010: C:\Documents and Settings\user\Local Settings\Application Data\Microsoft\Outlook
- For Outlook 2007: C:\Documents and Settings\user\Local Settings\Application Data\Microsoft\Outlook
- For Outlook 2003: C:\Users\username\Documents\Outlook Files\
- For Outlook XP: C:\Documents and Settings\Username\Local Settings\Application Data\Microsoft\Outlook
- For Outlook 2000: C:\Documents and Settings\Username\Local Settings\Application Data\Microsoft\Outlook
Step 2: Download, install the program and Run it.
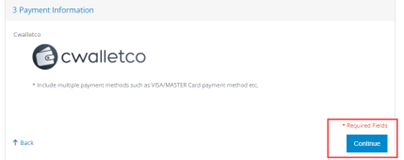
Step 3: Choose the file encrypted by the virus and select Next.
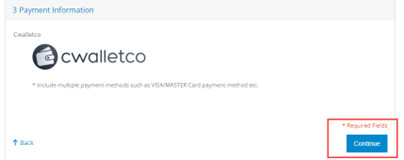
Step 4: Select Recovery Mode and Click Next.
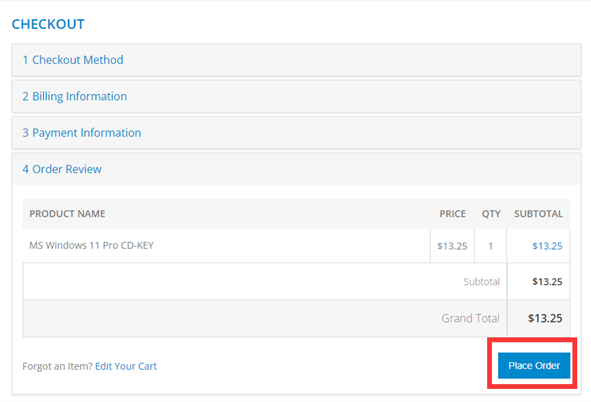
Step 5: Click on Yes to begin recovery.
Step 6: Inspect the data preview and click Next to save the recovered file to a new location.
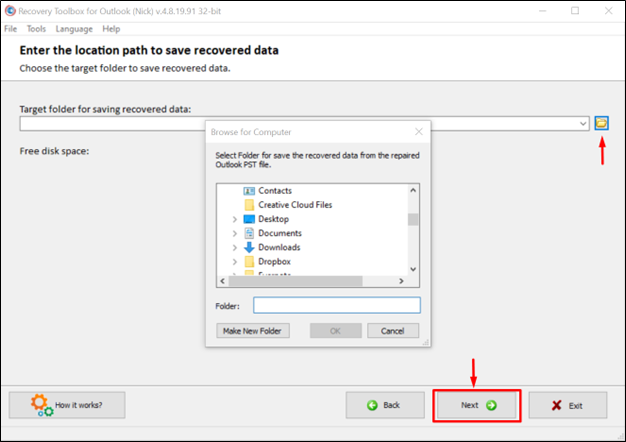
Step 7: Enter the location to save the .pst file and click Next.
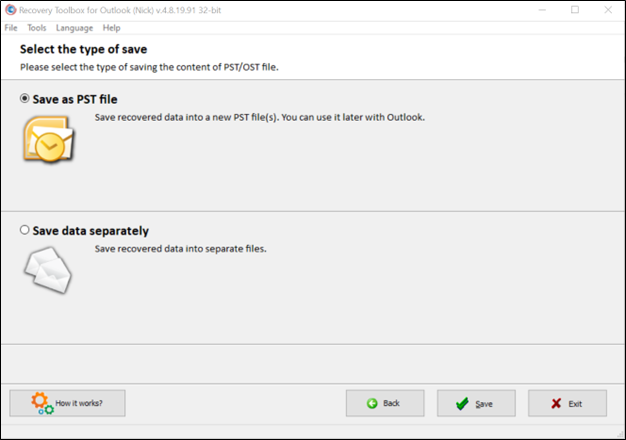
Step 8: Save the recovered data as the new .pst file.
Step 9: After checking the successful recovery results, click Finish to exit the Recovery Toolbox for Outlook tool.
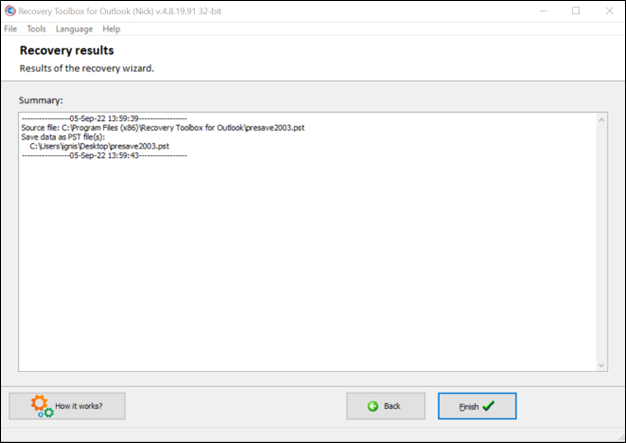
It is important to note that you should substitute the damaged file with a recovered one. You can also add the recovered .pst file to the list of data files in Outlook. This is how you do it for these versions of Outlook: 2021, 2019, 2016, and 2013:
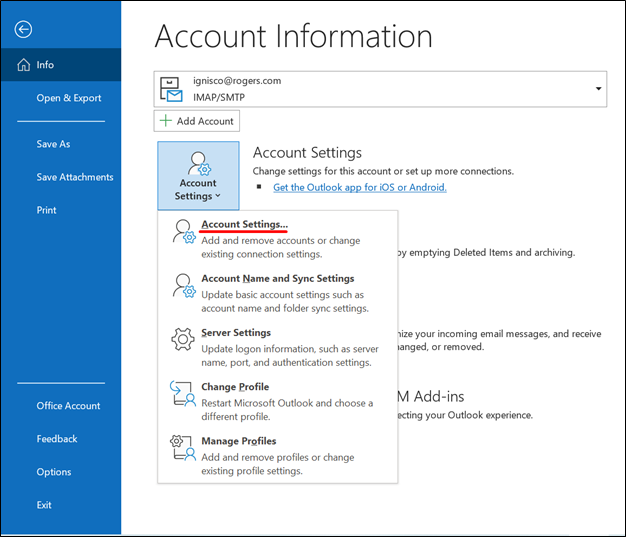
- Choose the menu item File | Info.
- Next, click the button Account Settings.
- Finally, choose Account Settings in the pop-up menu.
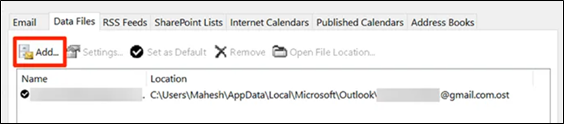
- Choose the Data Files tab and click Remove.
- Click Open File Location and select the recovered file. Click Set as Default.
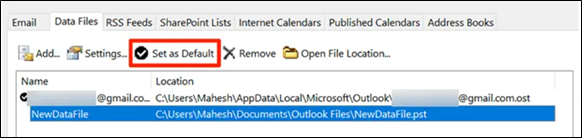
Once you have reached this stage, you have successfully fixed the issue.
Conclusion
The Recovery Toolbox for Outlook uses high-grade algorithms and procedures in analyzing, fixing, and restoring files, irrespective of the problem or its cause– i.e., viruses, bugs, hardware damage, network problems, HDD damage, etc.
The tool has the following advantages:
- With the tool, you can fix Microsoft Outlook files with .PST extension across different versions (ANSI (Outlook 97-2003), Unicode (2007 and above)).
- The recovery tool allows you to repair and recover files protected by a password.
- With the tool, you can recover damaged (or attacked) OST files irrespective of their versions.
- The tool allows you to repair encrypted files with the .PST extension.
- You can quickly repair PST files of different sizes, up to 180 Gigabytes, and more.
The Recovery Toolbox for Outlook is very efficient for repairing and recovering every kind of file and data on Microsoft Outlook. You can use it to easily access damaged, password-protected, and encrypted files like contacts, tasks, documents, etc. The tool is easy to use and is effective both online and offline.
SentinelOne Completes Acquisition of PingSafe
COMPANY NEWS: Combination creates new leader in cloud security with a fully integrated, AI-powered platform that protects entire enterprise
Vulnerabilities on Bosch Rexroth Nutrunners May be Abused to Stop Production Lines, Tamper With Safety-Critical Tightening's
COMPANY NEWS UPDATE : As production lines become increasingly reliant on interconnected computer systems, the risk of cybercriminal exploitation looms large.
Security Audits and Penetration Testing
In the past, penetration testing and regular security audits were reserved for highly skilled experts. However, nowadays, they are now a matter for the average security team, or at least they should be.
Smarter student journeys and stronger cyber-security: Where the higher education sector will concentrate its ICT investment in 2024
GUEST OPINION: Connecting with students digitally and keeping their data safe will be key priorities for Australian universities over the next 12 months.
Smarter student journeys and stronger cyber-security: Where the higher education sector will concentrate its ICT investment in 2024
GUEST OPINION: Connecting with students digitally and keeping their data safe will be key priorities for Australian universities over the next 12 months.
Hey threat actors… we see you!
GUEST OPINION: A huge cybersecurity threat exists because threat actors are hiding in one of the very mechanisms created to protect us — encryption. That’s why my company has launched a breakthrough cybersecurity technology for the world, specifically designed to eliminate this blind spot.
Dynatrace Achieves AWS Security Competency
COMPANY NEWS: Recognises the company’s unified observability and security platform as a trusted solution for helping organisations identify, resolve, and defend against threats to their AWS environments
Vendor Responses to Australian Cyber Security Strategy Launch
GUEST OPINION: Responses from BeyondTrust, Check Point Software Technologies, Secure Code Warrior and WatchGuard Technologies in relation to this week’s Federal Government Australian Cyber Security Strategy 2023-2030 launch.
The cyber defence boost coming to Australian travel apps
GUEST OPINION: As booking app usage soars, developers are having to re-assess their security and adopt more cyber defence automation to combat rising threats.
WEBINARS & EVENTS
- OutSystems Announces ONE 2025: The Future of AI-Powered Application and Agent Development Unveiled
- 8 DAYS TO GO - Maximising Cloud Efficiency - How to do more with Less
- 12 DAYS TO GO - Maximising Cloud Efficiency - How to do more with Less
- UiPath to Unveil Latest Agentic Automation Solutions at Agentic AI Summit
- ALL WELCOME - 6 DAYS TO GO - AI in Action is your opportunity to gain actionable strategies for deploying scalable, reliable AI solutions that drive measurable business outcomes.
CYBERSECURITY
- Kaseya unveils Spring 2025 innovations, showcasing ‘AI-Driven innovations’ across IT management and cybersecurity
- Australians warned: 'Election scams on the rise' following U.S. Trends
- The Blue Team Burnout and How to Prevent It
- Report reveals record-breaking year for Microsoft vulnerabilities
- SentinelOne Recognised as the Best Performing Vendor in Frost Radar Endpoint Security, 2025
PEOPLE MOVES
- Gerry Sillars is Bolstering Semperis’ Identity-Driven Cybersecurity Efforts in Asia Pacific and Japan
- Tenable Appoints Steve Vintz and Mark Thurmond as Co-CEOs
- Barracuda Appoints Ketan Tailor as Chief Customer Officer
- SYSPRO appoints Leanne Taylor as Chief Revenue Officer
- Cloudian appoints new APJ Channel and Marketing Directors
GUEST ARTICLES
- Logicalis expand APAC SOC services with launch of Cisco MXDR
- OutSystems Announces ONE 2025: The Future of AI-Powered Application and Agent Development Unveiled
- National 'research and development crisis' calling for Team Australia
- AI Hype Cycle meets Reality for Construction Industry
- New Book from Boomi Warns: AI Will Fail Without a Digital Infrastructure Overhaul
- Research Firm Names Datadog an AIOps Market Leader
- Why finance teams can’t afford to ignore shifting spend trends and artificial intelligence innovation
-
Why I switched from AliExpress to local suppliers for Amazon dropshipping
GUEST OPINION: My dropshipping journey with Amazon began like most…
Guest Opinion
- New Book from Boomi Warns: AI Will Fail Without a Digital Infrastructure Overhaul
- Why finance teams can’t afford to ignore shifting spend trends and artificial intelligence innovation
-
Why I switched from AliExpress to local suppliers for Amazon dropshipping
GUEST OPINION: My dropshipping journey with Amazon began like most…
-
How social media automation can boost your sales
GUEST OPINION: Social media isn’t just for brand awareness anymore.…
-
5 Secrets to Faster Innovation in IT You Can't Avoid to Ignore
GUEST OPINION: Imagine this scenario: Two competing financial institutions decide…
-
This is why great content alone won’t get you found on Google
GUEST OPINION: You just dropped what you know is a…
- Why Limiting Your Hiring to One Country Is Holding Your Business Back
- Data Management – It’s a High-Stakes Game
ITWIRETV & INTERVIEWS
- Amazon CISO CJ Moses gives rare interview
- Matt Salier explains the Australian Cyber Collaboration Centre's voluntary data classification framework
- Qualys CEO Sumedh Thakar explains the Risk Operations Centre (ROC)
- iTWire talks to SailPoint about identity management in the Enterprise
- How Blue Yonder is applying AI and innovation to solve supply chain challenges
RESEARCH & CASE STUDIES
Channel News
Comments
-
Re: iTWire - Can cyber security be a platform for innovation and growth?
Most cybersecurity is making up for weak platforms. We need to address the fundamentals, design platforms that prevent out-of-bounds access[…]
-
Re: iTWire - Why Software Developers Need a Security ‘Rewards Program’
For most developers the security/performance trade off is still the hardest one to tackle, even as the cost of processing[…]
-
Re: iTWire - The Risc-V architecture that can shape the future of computing
RISC has been overhyped. While it is an interesting low-level processor architecture, what the world needs is high-level system architectures,[…]
-
Re: iTWire - Is Linux finally ready to storm the mainstream?
There are two flaws that are widespread in the industry here. The first is that any platform or language should[…]
-
Re: iTWire - Transport for NSW and HCLTech expand digital transformation partnership
Ajai Chowdhry, one of the founders and CEO of HCL is married to a cousin of a cousin of mine.[…]
































