The company has been reported by its own publications as not having received any ransom note as yet. However, one of its own publications, the Australian Financial Review, had this [see tweet below] in a report filed overnight:
"While Nine is understood to have received no ransom demand to unlock its targeted systems, an email to staff suggested that some files associated with a known ransomware strain called MedusaLocker could have been behind the attack.
"Staff were instructed to check their laptops for the presence of a file called Recovery_ Instructions.html. Cyber security experts identified this as a calling card of Medusa, and said it represented a tough recovery task for Nine’s tech staff."
|
|
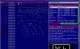
Wait, so there's no "ransom note" in the AU event, but victims were instructed to check for "Recovery_Instructionms.html", which kind of sounds like a ransom note....https://t.co/3QMiHwIBDL pic.twitter.com/lm5cyr1vKH
— Joe Słowik ? (@jfslowik) March 29, 2021
Additionally, the main evening news from Channel Nine on Monday [see tweet with video below] made the claim that no ransom has been demanded yet.
DomainTools infosec researcher Joe Slowik, who highlighted this in a tweet, said: "Wait, so there's no "ransom note" in the AU event, but victims were instructed to check for "Recovery_Instructions.html", which kind of sounds like a ransom note...."
He linked to VirusTotal detection of MedusaLocker, adding: "Timing, family, and other info would seem to indicate this is a fit although file extension is off..."
Slowik also posted the ransom note that was generated by MedusaLocker.
The AFR said this advice given to staffers put paid to any possibility that the attack had been driven by Nine's publishing of reports about North Korea and Russia, a theory that the company floated on its evening news bulletin on Monday.
Russia and North Korea have been singled out as suspects in the biggest-ever cyber attack on an Australian media company – and experts say it could be retaliation from recent attention by the Nine Network. @DamoNews #9News pic.twitter.com/6YzQuUVjj7
— 9News Australia (@9NewsAUS) March 29, 2021
According to Cisco's Talos Intelligence Group, since it was first spotted in 2019, there have been several variants of MedusaLocker that have been observed.
Talos researcher Edmund Brumaghin wrote: "However, most of the functionality remains consistent. The most notable differences are changes to the file extension used for encrypted files and the look and feel of the ransom note that is left on systems following the encryption process."
He said that while MedusaLocker had similar functionality to most other Windows ransomware strains, there were some features which set it apart:
"MedusaLocker can encrypt the contents of mapped network drives that may be present on infected systems;
"It manipulates Windows functionality to force network drives to be remapped so that their contents can also be encrypted;
"The malware uses ICMP sweeping to profile the network to identify other systems that can be used to maximise the likelihood of a ransom payment."
Contacted for comment, Brett Callow, a seasoned ransomware researcher at New Zealand-headquartered security shop Emsisoft, said: "While there's been speculation that a nation-state actor was responsible — perhaps even at the behest of [Vladimir] Putin himself — there would appear to be little evidence to actually back that up.
"A far more likely, albeit much less exciting, explanation is that the attack was the work of a vanilla group of for-profit criminal scumbags who snuck in via a phishing email or unpatched system. That's how attacks such as this typically unfold."
The attack was made public on Sunday morning, a day on which Nine could not broadcast its popular NRL Sunday Footy Show, though it managed to show the afternoon's rugby league games.
iTWire has contacted Nine for comment. The only public statement that the company has made so far is to acknowledge that an attack occurred.