The San Jose, California company sought a trial by jury to decide the charges which were filed by the law firm Clare Locke LLP. [corrected].
The case against Krebs was filed in the US District Court for the eastern District of Virginia, Alexandria Division, on Tuesday.
Krebs wrote a story in March last year — which he later updated — which was fed to him by an ex-employee of Ubiquiti who was himself involved in the data theft and extortion bid, while he masqueraded as a whistleblower and anonymous attacker. The ex-worker, Nickolas Sharpe, was indicted by the US Department of Justice in December last year.
In its complaint, Ubiquiti said contrary to what Krebs had reported, the company had promptly notified its clients about the attack and instructed them to take additional security precautions to protect their information.
"Ubiquiti then notified the public in the next filing it made with the SEC. But Krebs intentionally disregarded these facts to target Ubiquiti and increase ad revenue by driving traffic to his website, www.KrebsOnSecurity.com," the complaint alleged.
|
|
 The Ubiquiti complaint said when the DoJ issued a media release about Sharp's indictment, Krebs did not change his story in any way. "Krebs reviewed the press release and he knew that his sole source had been indicted for his criminal involvement in the cyberattack," it claimed.
The Ubiquiti complaint said when the DoJ issued a media release about Sharp's indictment, Krebs did not change his story in any way. "Krebs reviewed the press release and he knew that his sole source had been indicted for his criminal involvement in the cyberattack," it claimed.
"Despite these damming facts, Krebs published a story on his blog the next day doubling down on his false accusations against Ubiquiti and intentionally misleading his readers into believing that his earlier reporting was not sourced by Sharp, the hacker behind the attack.
"Instead of acknowledging that the source from his previous story was indicted by federal prosecutors for his crimes against Ubiquiti, Krebs calls Sharp 'a Ubiquiti employee' when referencing Sharp’s contributions to his reporting.
"But in the very next sentence, Krebs describes Sharp as 'a former Ubiquiti developer' who 'was arrested and charged with stealing data and trying to extort his employer while pretending to be a whistleblower'.”
According to the indictment issued by the DoJ against Sharp in December 2021, after publication of the articles in question on 30 and 31 March, Ubiquiti's stock price fell by about 20% and the company lost more than US$4 billion (A$5.32 billion) in market capitalisation.
The DoJ did not mention Sharp's employer, but Sergiu Gatlan, a reporter with the website Bleeping Computer, wrote that the details around the incident perfectly matched existing information on the Ubiquiti breach and also on Sharp's LinkedIn account.
The Krebs' report appeared to have been the original with four others — in the Washington Post, Cybereason, Apple Insider and ZDNet — citing Krebs' report as the source in their reports, all of which appeared on or around 30 March.
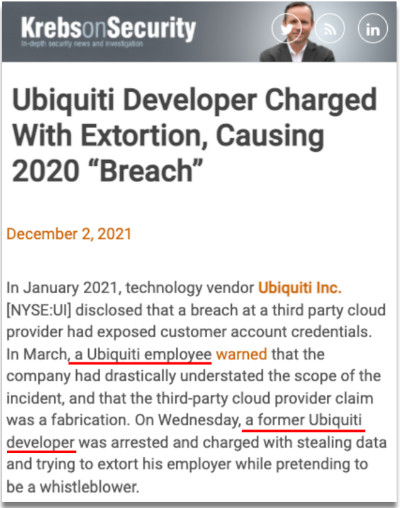
The complaint charged that while the DoJ indictment was central to a follow-up story that Krebs published in December [screenshot above, right], he continued to repeat the false assertion that “[i]n March, a Ubiquiti employee warned that the company had drastically understated the scope of the incident, and that the third-party cloud provider claim was a fabrication".
The complaint alleged Krebs had intentionally misrepresented the truth because he had a financial incentive to do so, adding, "His entire business model is premised on publishing stories that conform to this narrative. Despite overwhelming facts showing that his reporting is pure fiction, Krebs has refused to retract or correct his disinformation campaign against Ubiquiti".
The complaint detailed the incident that led to the first story, saying that it had found suspicious activity on its cloud infrastructure on 28 December 2020 and then put together a team, which included Sharp, to investigate.
"A short time after Ubiquiti discovered the attack, the unknown 'hacker' sent an anonymous ransom note via the platform Keybase," the complaint said. "The 'hacker' claimed that he accessed Ubiquiti’s systems as an outsider and [had] taken information from Ubiquiti (including elements of its source code).
"The 'hacker' also demanded 25 bitcoin from Ubiquiti for the return of the data and the hacker’s silence and an additional 25 bitcoin for the hacker to reveal the location of a second 'backdoor' access point in Ubiquiti’s system. At the time, 50 bitcoin was worth approximately US$2 million." (A$2.66 million)
The second backdoor was identified by the investigators, hence Ubiquiti said it refused to pay any ransom and informed its customers about the incident, advising that they take steps to ensure they were safe.
The complaint said the company also informed investors and the public about the ransom note, and law enforcement as well. As Ubiquiti continued to investigate the ransom note and the suspicious activity on its cloud infrastructure, it said many factors led it to believe the attack was an inside job and that Sharp was behind the blackmail scheme.
"Through its investigation, Ubiquiti learned that Sharp had used his administrative access codes (which Ubiquiti provided to him as part of his employment) to download gigabytes of data. Sharp used a Virtual Private Network (VPN) to mask his online activity, and he also altered log retention policies and related files to conceal his wrongful actions," the complaint alleged.
"Ubiquiti shared this information with federal authorities and the company assisted the FBI’s investigation into Sharp’s blackmail attempt. The federal investigation culminated with the FBI executing a search warrant on Sharp’s home on 24 March 2021."
The complaint then went into detail about how Sharp contacted Krebs and how the story came to be published.
Krebs was accused of two counts of defamation, with Ubiquiti seeking a jury trial and asking for a judgment against him that awarded compensatory damages of more than US$75,000, punitive damages of US$350,000, all expenses and costs including lawyers' fees and any further relief deemed appropriate by the court.
iTWire has contacted Krebs and the law firm Clare Locke LLP for comment.