"Findings from the SophosLabs 2018 Malware Forecast show that attacks on Mac, iOS, Android and Linux have increased over the last year. Perhaps unsurprisingly, we've seen Windows hit the hardest by malware, followed by an explosion in Android malware and continued efforts to infect Mac computers and iOS users. A trend that is only due to continue into 2018, as hackers seek to follow the users of most value, regardless of the systems they use," Sophos vice-president of product Marty Ward told iTWire.
"In fact, Australia is already number three in the world for malware on the Mac platform; ahead of Japan, Russia, China and Germany. With this in mind, Mac and iOS users in particular must remember that most ransomware is proliferated via social engineering, in particular via phishing emails, which are not specific to a particular operating system. Users must update their systems regularly, create backup copies of their data and deploy real-time threat protection in order to stay protected."
While admitting that "It's impossible to predict the future with 100% accuracy", the security vendor thinks four current trends will persist into next year.
Ransomware
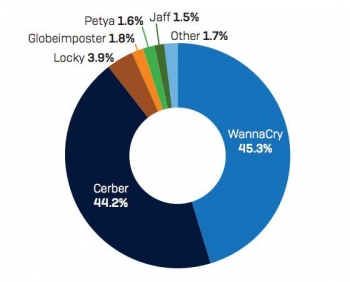
WannaCry and Cerber accounted for almost 90% of malware attacks blocked by Sophos between April and October. WannaCry's success was largely due to its ability to worm its way from one computer to another. The vulnerability it relied on has largely been patched, but Sophos is concerned that there will be further leaks of exploits used by government agencies, which will be used to drive fresh attacks in 2018.
|
|
"Even though our customers are protected against it and WannaCry has tapered off, we still see the threat because of its inherent nature to keep scanning and attacking computers.
"We're expecting cyber criminals to build upon this ability to replicate seen in WannaCry and NotPetya, and this is already evident with Bad Rabbit ransomware, which shows many similarities to NotPetya."
The significance of Cerber is that it is ransomware as a service (RaaS), and its creators are actively developing it to circumvent defensive measures.
"This Dark Web business model is unfortunately working and similar to a legitimate company is likely funding the ongoing development of Cerber. We can assume the profits are motivating the authors to maintain the code," said Palotay.
Windows malware will continue to predominate.
Android malware
Ransomware "remains a big problem for Android users", Sophos said.
SophosLabs expects to process 10 million suspicious Android apps by the end of 2017, an increase of more than 17% over 2016. And the number of "threats" found on Google Play during the first nine months of the year doubled to 32, including what appeared to be highly-targeted malware designed to monitor phone activity and exfiltrate app data.
Other examples of Android malware included click fraud, DDoS bots, and ransomware. Some ransomware actually encrypts files, others just lock the screen until a PIN is purchased and entered.
"One reason we believe ransomware on Android is taking off is because it's an easy way for cyber criminals to make money instead of stealing contacts and SMS, popping ups ads or bank phishing which requires sophisticated hacking techniques," said SophosLabs security researcher Rowland Yu.
"It's important to note that Android ransomware is mainly discovered in non-Google Play markets - another reason for users to be very cautious about where and what kinds of apps they download."
Mac malware
Almost all of the Mac malware detected by Sophos falls into the "potentially unwanted programs" rather than full-blown malware. This includes applications such as MacKeeper and TuneUpMyMac.
Of that small proportion of 'real' malware, the most common examples are adware (programs that deliver additional advertising within a web browser), but the company also " intercepted several examples of Mac ransomware."
Interestingly, south-east Australia was one of the global hot spots for Mac threat activity, according to Sophos.
Windows threats
You've probably heard this before, but old vulnerabilities are still being exploited because Windows systems aren't being patched properly.
The second most common Windows Office exploit takes advantage of a vulnerability that was fixed in 2012. Others in the top ten date back to 2015, 2014, 2013, 2011, and even 2010.
But the current frontrunner is CVE-2017-0199, which was addressed in April 2017 and exploited relatively quickly after it became public knowledge. This vulnerability was even used by malware-creating tools that were made available free of charge.
"We expect to see increasingly easier exploits distributed on the Dark Web," said Sophos, predicting "chances are better than average that attackers will target companies that are slow in installing" the October 2017 fix for CVE-2017-11826 affecting Office 2010 and other Microsoft software.
The SophosLabs 2018 Malware Forecast is available here.