Broadly, there are two types of audit that any VPN provider should undertake.
Security audit: These are conducted by some third-party auditor and will identify whether a VPN platform has any vulnerabilities and what data it logs.
Privacy policy/no logs audit: The auditor will review a provider’s no-logs policy, looking at their connection and usage logs, as well as any data saved on their servers. They will then release a report detailing their findings, outlining whether the policy matches the data held on their server.
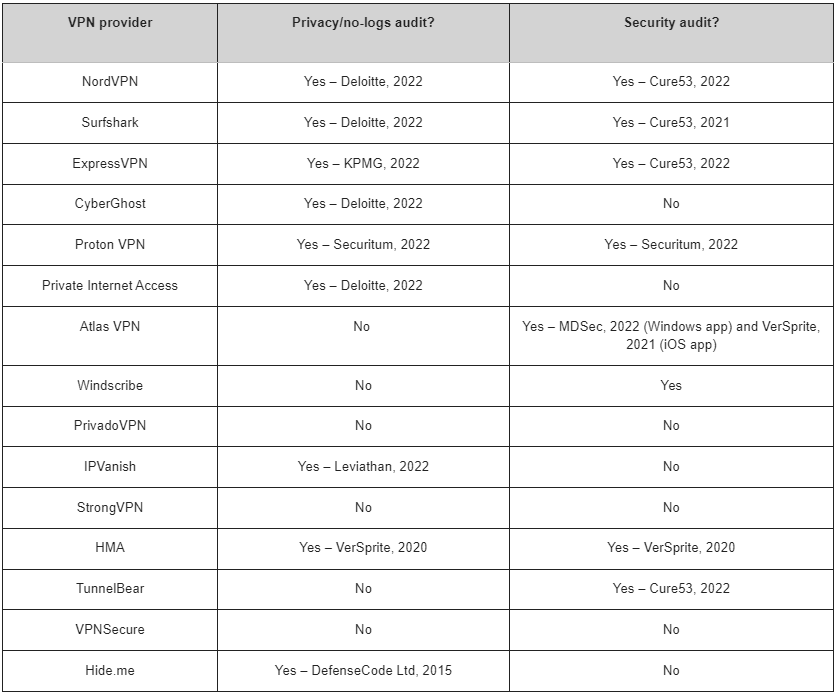
It would be reasonable to expect that audits were conducted yearly by external companies specialising in VPN privacy and security. These include the notable ‘big four’ consulting firms - Deloitte, KPMG, PwC, EY, as well as specialist cybersecurity firms such as Cure53, MDSec, VerSprite, Securitum, and Leviathan.
Recent research by UK company Independent Advisor has found that things perhaps aren’t as rosy as we might hope. In particular, the report draws attention to the very clear difference between free and paid VPN services. “As tempting as a free VPN option may be, the way these providers usually make money is unfortunately by selling data to third-party advertisers, and they often don’t have the money to invest in better security infrastructure, making users more vulnerable to data breaches and related cybercrimes.” Of course this is a very general observation, but it should give users pause for thought.
|
|
“Many VPN providers claim to maintain a no-logging policy, which generally means at a minimum they do not store any data relating to user internet activity,” notes Nick Seaver of Deloitte. “The data that is logged by some VPN services can include the time users connect and disconnect from the VPN, their real IP address and the address of the VPN server, the volume of data transmitted and connection information, such as your device, operating system and VPN software.
“For people who are using VPNs to keep their online activities confidential and secure, the provider’s logging policies are important and it’s a good idea to read the policy carefully. The policy should clearly explain what data the VPN does and does not log, for what purpose and the duration the logs are kept. Logging policies potentially enable the provider to track and store information about users’ internet activity.
“If providers log your activities in detail, they can track your internet activity and potentially share it with others. If users want a VPN for privacy and security, it’s important to choose a provider with an appropriate no-logging policy.”
The following chart is an extract from the report. It’s not comprehensive – iTWire is aware of a number of VPN solutions that are not included. Perhaps if readers wish to use a service not shown here, they should seek out audit information on the provider’s web site.
Of course, the opposite is true; just because a service is audited, doesn’t mean that some issue may be discovered in the future, particularly within the domain of the security audit.