The recently released OWASP Top 10 - a summary of the primary attack vectors used by ne'er-do-wells has taken a somewhat different approach than in previous years. As the report states, "This instalment of the Top 10 is more data-driven than ever but not blindly data-driven. We selected eight of the ten categories from contributed data and two categories from the Top 10 community survey at a high level. We do this for a fundamental reason, looking at the contributed data is looking into the past. AppSec researchers take time to find new vulnerabilities and new ways to test for them. It takes time to integrate these tests into tools and processes. By the time we can reliably test a weakness at scale, years have likely passed. To balance that view, we use an community survey to ask application security and development experts on the front lines what they see as essential weaknesses that the data may not show yet."
The report continues, "There are three new categories, four categories with naming and scoping changes, and some consolidation in the Top 10 for 2021. We've changed names when necessary to focus on the root cause over the symptom."
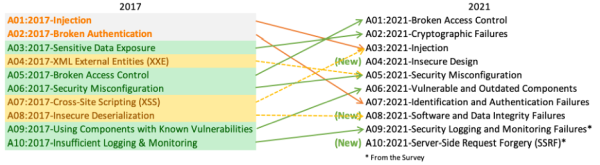
Matias Madou, Co-founder and CTO of Secure Code Warrior notes, "The latest OWASP Top 10 release revealed some significant shake-ups, with Injection flaws finally being knocked from the top spot in favour of Broken Access Control vulnerabilities. This is big news for sure, but the more important consideration is that the OWASP list is replacing most single attack techniques with entire families of vulnerabilities.
|
|
"It has become increasingly apparent that core security design is failing. This gives way to architectural vulnerabilities that can be advantageous to threat actors—especially if they go unpatched after the security flaw in a particular version of an application is made public.
"The trouble is, few engineers are given training that goes beyond the basics. Fewer still have their knowledge and practical application expanded beyond localised, code-level bugs that are typically developer-introduced in the first place. For every code-level weakness found, more complex architectural flaws will go unnoticed by most of the security tech stack, no matter how many automated shields and weapons are in the arsenal. The refreshed OWASP Top 10 list proves training horizons for developers need to expand rapidly to achieve what robots cannot."
A spokesperson from Skillsoft agrees, "Knowing learners are increasing the amount of security training they're doing is valuable, but it begs the question of where they're spending their time. Looking at the 10 most frequently completed security courses so far in 2021, OWASP Top 10 related lessons take the lead spot, followed by cloud security fundamentals, which could be attributed to the COVID-19 pandemic spurring a rapid global shift to the cloud."
"But," continues Madou, "like all things worth fighting for, the 2021 list represents a foundation the industry must build upon for truly top-notch security practices—not an end-game, and certainly not something that can happen overnight. The threat landscape is so fast-paced that there must be a deeper and more specific plan to upskill developers in security. Failure to do so will inevitably lead to missed opportunities to remediate threats to an organisation.
"If the cybersecurity skills gap is ever going to shrink, we must start to cast a wider net with developer upskilling and have a positive impact on software safety in the face of crazy demand for secure code."
Also, for those readers wanting a simplified view of the OWASP Top 10, Immersive Labs has developed a 'cheat sheet.'





































