Singapore-based Group-IB listed the Equation Group, which is generally acknowledged as being a part of the NSA. It was originally discovered and named by Russian security outfit Kaspersky. In its latest Hi-Tech Crime Trends report for 2019-20, Group-IB pointed out that the Equation Group was operating against Russia and countries formed from the break-up of the former Soviet Union.
Of itself, Group−IB says it is a leading provider of high‐fidelity adversary tracking and threat attribution framework, and best‐in‐class anti‐APT and online fraud prevention solutions
It claims to have been in business for 16 years, with more than 60,000 hours of incident response experience, says it has carried out more than 1000 cyber crime investigations globally and has more than 360 top-drawer cyber security experts on its staff.
|
|
When Kaspersky described the Equation Group, it characterised the entity as the one of the most sophisticated cyber attack groups in the world and "the most advanced ... we have seen", operating alongside but always from a position of superiority with the creators of Stuxnet and Flame.
Kaspersky says most of the Equation Group's targets had been in Iran, Russia, Pakistan, Afghanistan, India, Syria, and Mali.
According to Wikipedia, the name Equation Group was chosen because of the group's choice of sophisticated encryption methods in their operations. By 2015, Kaspersky had documented 500 malware infections by the group in at least 42 countries, while acknowledging that the actual number could be in the tens of thousands due to its self-terminating protocol.
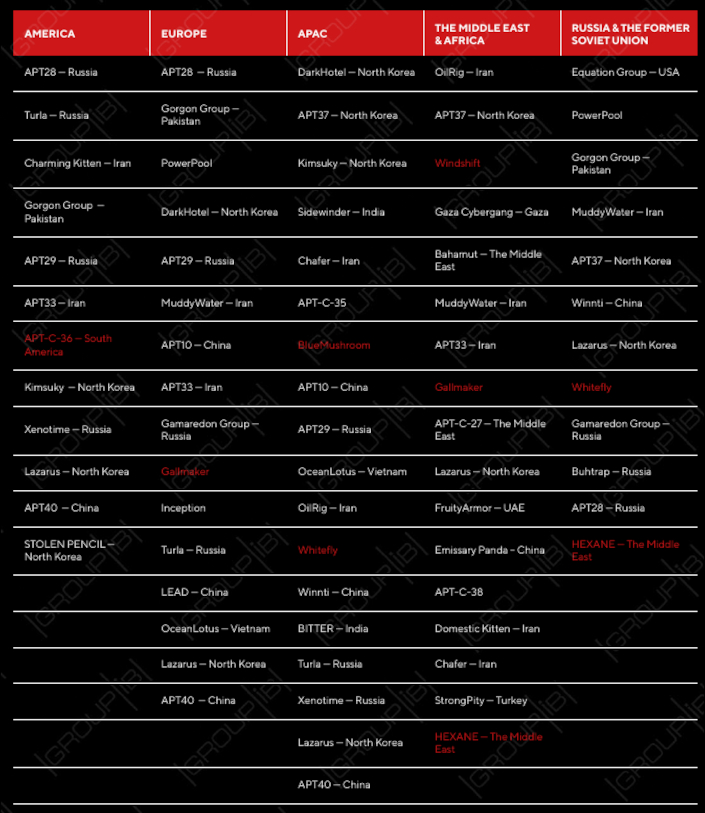
The geographical areas that various APTs focus on. Courtesy Group-IB
In 2017, WikiLeaks published a discussion held within the CIA on how it had been possible to identify the group. One commenter wrote that "the Equation Group as labelled in the report does not relate to a specific group but rather a collection of tools" used for hacking.
Kaspersky announced the existence of the Equation Group during its annual summit in Mexico in 2015, saying the group had been active at least since 2001 and had more than 60 actors. The malware it used, dubbed EquationDrug and GrayFish, was found to be capable of reprogramming hard disk drive firmware.
Because of the advanced techniques involved and high degree of covertness, the group is suspected of ties to the NSA, but Kaspersky has not identified the actors behind the group.
In August 2016, a group calling itself The Shadow Brokers, widely suspected to be NSA insiders, released stolen exploits from the Equation Group on the web. Kaspersky cited similarities between the stolen code and earlier known code from the Equation Group malware samples it had in its possession, including quirks unique to the Group's way of implementing the RC6 encryption algorithm, and concluded that this announcement was legitimate.
The stolen files date from as recent as June 2013, thus prompting NSA whistleblower Edward Snowden to speculate that a likely lockdown resulting from his leak of the NSA's global and domestic surveillance efforts stopped The Shadow Brokers' breach of the Equation Group.
Exploits against Cisco Adaptive Security Appliances and Fortinet's firewalls were featured in some malware samples released by the Shadow Brokers. EXTRABACON, a Simple Network Management Protocol exploit against Cisco's ASA software, was a zero-day exploit at the time of the announcement.
Network equipment maker Juniper also confirmed that its NetScreen firewalls were affected. The EternalBlue exploit was used to conduct the damaging worldwide WannaCry ransomware attack in May 2017.
Apart from the Equation Group, the Group-IB report also lists what it claims are APTS from Russia, Iran, North Korea, Pakistan, the Middle East, China, Gaza, Vietnam, the UAE, Turkey and India. Several of these groups have more than geographical area of operation, according to Group-IB.
The report said the key threat to telecommunications networks was hijacking of the border gateway protocol, with nine of the APTs posing a threat to the sector, more than the number of groups that were considered a threat to the financial sector.
The firm said that as 5G networks expanded, the cyber security problems of each company's gear would reflect their share of the market.
"In a few years, telecom companies will struggle to detect hardware and firmware backdoors in 5G infrastructure equipment," Group-IB predicted.
"Many telecom operators are managed service providers and provide security services to government and commercial organisations. Threat actors will attack operators to penetrate the networks they protect."
The 63-page Group-IB report said that only two Russian-linked groups showed an interest in attacking the energy sector by compromising networks and using traditional malware.
Regarding the financial sector, the report said SilentCards was a new group that was focused on attacking banks in Africa.

The trend of attacks had changed since 2017, Group-IB claimed, pointing to big ransomware attacks like WannaCry, NotPetya and Bad Rabbit in 2017, followed by side-channel attacks and targeting vulnerabilities in processors the following year and moving to overt military operations in cyber space in 2019.
One incident of sabotage was noticed in March 2019 when Simón Bolívar Hydroelectric Plant, also known as the Guri Dam, was attacked. This resulted in a mass-scale blackout in Caracas and 22 of the 23 states. The Russian news agency TASS, cited the Venezuelan Communications Minister Jorge Rodriguez as saying there had been a cyber attack against the automated control system. This is the first time large parts of a country have been left without power for many days due to an attack of this kind.
A second incident involved a group affiliated to the Palestinian group Hamas. Group-IB said cited Israeli sources as saying on 4 May 2019, hackers tried to carry out a cyber attack but did not reveal details. The Israel Defence Forces launched an air strike on a building in the Gaza Strip in retaliation, where the hackers; headquarters is believed to have been located. This is said to be the first time that a missile strike has been launched in response to a cyber attack.
A third incident was recorded in June 2019. On 20 June, Iran's Islamic Revolutionary Guard Corps shot down a US drone. The US retaliated a few days later by launching a cyber attack on IRGC's missile control systems.
As this kind of attack needs months of preparation, the systems had probably been compromised some time ago, Group-IB reasoned.
BGP hijacking occurs when traffic is directed to the wrong sources. When it came to inter-carrier routing, carriers (and content providers like Google, Facebook etc) often need to send traffic to each other.
Launtel ISP chief Damian Ivereigh explained it this way: "They rely on a protocol called BGP — Border Gateway Protocol — which essentially allows each carrier to broadcast to each other what IP address ranges (called 'prefixes') should be sent to them. We, for example, announce to the world that any traffic for the IP address range 103.216.190.0 to 103.216.191.255 should be sent to us."
The security of the process was "not great" and one carrier could announce incorrect prefixes and effectively take over the address ranges of another provider (and take them down).
"This is limited only by the level of trust that each carrier places in another carrier when they receive an advertisement.
Group-IB listed three BGP incidents in 2018 and 2019 which had affected traffic on the Internet. On 25 November 2018, a small Russian operator Krek made a mistake in its BGP configuration which led to between 10% and 20% of Russian Internet users losing access for more than an hour.
Companies like Amazon, YouTube, Russian social network VK and online video streaming service ivi.ru and a number of other organisations were also affected.
The same month, MainOne, a Nigerian ISP, made a configuration error that changed routes in such a way that traffic to Google services was sent to China, with a total of 180 prefixes being affected. The problem was fixed after 74 minutes.
A third incident, on 6 June 2019, the Swiss company Safe Host caused a leak of 70,000 routes to China Telecom. Swisscom, the Dutch ISP KPN and French ISPs Bouygues Telecom and Numericable-SFR were all affected for two hours.
Group-IB said during the period covered by the report, its researchers had analysed attacks carried out by 38 groups from Russia, North Korea, Pakistan, China, Vietnam, Iran, the US, the UAE, India, Turkey and unspecified South American countries.
"It is important to note that there is still no public information about attacks originating from developed countries. This again confirms that well-orchestrated attacks are difficult to detect or attribute to a specific group or country," the report said.
Group-IB said its previous report had identified BIOS/UEFI attacks as a prominent trend, with experts predicting that the main targets would be firmware and motherboard makers in the Asia-Pacific region where many big companies have their production facilities.
Soon after the report was published, news of a malware campaign called Operation ShadowHammer came to light, with malware being delivered through the ASUS Live Update, a legitimate utility that automatically updates BIOS, UEFI, drivers and applications.
The malicious utility was signed with a legitimate certificate from ASUSTeK Computer and hosted on an ASUS server.
In July 2018, experts found a new malware campaign involving the Plead backdoor, which was digitally signed using a valid D-Link Corporation certificate. At the end of April 2019, these experts identified multiple attempts to deploy the same malware in an unusual way. The Plead backdoor was created and executed by a legitimate process named AsusWSPanel.exe.
The executable file was digitally signed by ASUS Cloud Corporation. Plead malware has always been most widely deployed in Taiwan.
In December 2018, Chinese attackers reportedly infiltrated the networks of Hewlett Packard Enterprise and IBM as part of the Cloudhopper campaign. By gaining access to the networks, they were subsequently able to break into computers belonging to HPE and IBM clients.
Cloudhopper compromised client data in 12 countries, including Brazil, Germany, India, Japan, the United Arab Emirates, Great Britain, and the United States.
The clients were from industries such as finance, electronics, medical equipment, biotechnology, automotive, mining, and oil and gas.
The Group-IB report also contains exhaustive details of JavaScript sniffers used to attack content management systems. details of other BGP attacks, details about attacks on ATMs and financial institutions and numerous other cyber heists, including PC banking trojans and bog-standard phishing exploits.









































