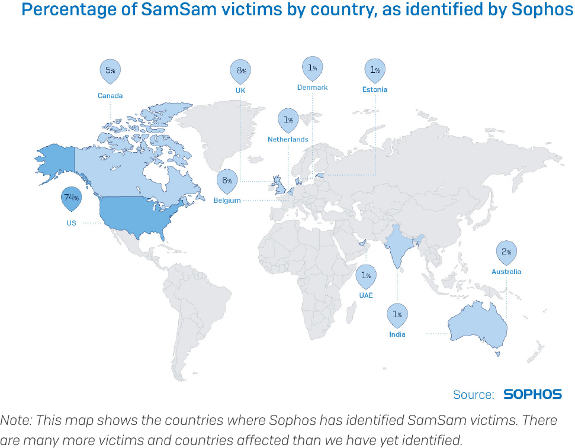
Researchers at the company said nearly three-quarters of known victims were in the US. Other countries targeted were Canada and the UK, while the Middle East had also been a target.
SamSam does not arrive via any vector like email; rather, the attacker gains access to a Windows machine through the Remote Desktop Protocol after using software like nlbrute to guess weak passwords.
Unlike ransomware such as WannaCry and NotPetya which spread on a network by using exploits, the human attacker is the one who spreads SamSam.
|
|
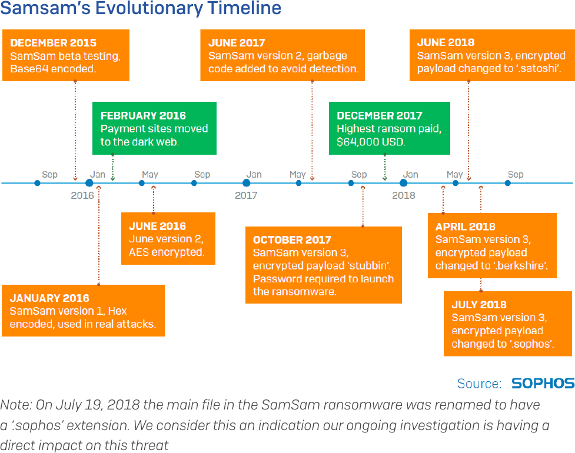
The biggest ransom that has been paid by an individual so far is US$64,000, Sophos said. But generally, SamSam's creators made money by demanding small amounts and infecting many users.
Great care was taken in infecting a Windows machine, with attacks being carried out late at night or early in the morning.
SamSam also differs from other ransomware in that it does not encrypt only document files, images and other personal or work data, but also files that are part of an application like Microsoft Office.
Given this, the Sophos researchers said, anyone who was only backing up their personal files would not be able to recover from a SamSam infection without re-imaging their PC.
"Every subsequent attack shows a progression in sophistication and an increasing awareness by the entity controlling SamSam of operational security," the researchers wrote. "The cost victims are charged in ransom has increased dramatically, and the tempo of attacks shows no sign of slowdown."
While SamSam has figured in media reports because of attacks on healthcare, government and education sectors, Sophos said most of the attacks were on private companies that were less inclined towards public disclosure.
"Based on our research of the Bitcoin addresses in ransom notes, we estimate that about 233 victims have paid a ransom to the attacker, but we don’t know the identities of all those victims," the researchers wrote.
Graphics: courtesy Sophos