The infection occurs while visiting a legitimate website. A malware dropper is downloaded from the threat actor’s infrastructure.
Super helpful #BadRabbit infection map by Avast.... pic.twitter.com/ulvIAnHvKg
— Chris Bing (@Bing_Chris) 24 October 2017
"No exploits were used, so the victim would have to manually execute the malware dropper, which pretends to be an Adobe Flash installer," Kaspersky said.
The company said it had detected a number of compromised website, all of which were news or media outlets.
|
|
Kaspersky Lab's Orkhan Mamedov, Fedor Sinitsyn and Anton Ivanov said that Bad Rabbit appeared to be similar to the NotPetya strain of ransomware that hit Europe in June.
"An interesting detail that we noticed when analysing the sample of this threat: it looks like the criminals behind this malware are fans of the famous books & TV show series Game Of Thrones. Some of the strings used throughout the code are the names of different characters from this series," they wrote.
You guise, I have live footage of #BadRabbit operating in the US! pic.twitter.com/EjHDwZsubD
— Jake Williams (@MalwareJake) 24 October 2017
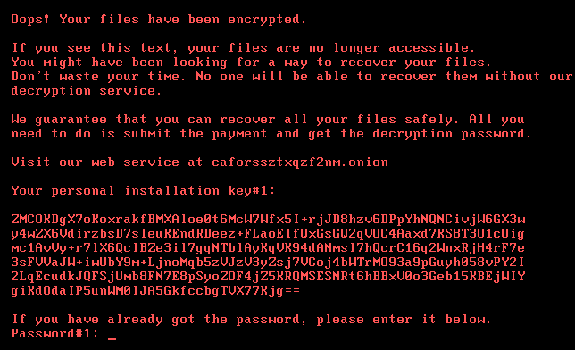
Cisco's Talos Intelligence Group said Bad Rabbit modified the master boot record of the infected system's hard drive to redirect the boot process into the malware author's code for the purposes of displaying a ransom note (seen above).
"The ransom note that is displayed following the system reboot is... very similar to the ransom notes displayed by other ransomware variants, namely Petya, that we have observed in other notable attacks this year," the Group said.











































