Project Managers are Headfirst in AI Adoption with Projected Investment Increase
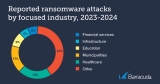
CapterraNew research finds that 44% of foiled ransomware attacks are caught during lateral movement
Barracuda NetworksGUEST RESEARCH: Barracuda Networks, a leading provider of cloud-first security solutions has released new research showing that lateral movement is the clearest sign of an unfolding ransomware attack, catching just under half (44%) of incidents. A quarter (25%) of incidents were detected when the attackers started writing or editing files, and 14% were unmasked by behavior that didn’t fit with known activity patterns. The findings are included in Barracuda’s annual Threat Spotlight on ransomware, which explores the main ransomware attack patterns over the last 12 months.
Tenable research discovers critical vulnerability in Microsoft Copilot Studio
TenableGUEST RESEARCH: Tenable — the exposure management company,has disclosed that its Tenable Research Team has discovered a critical information disclosure vulnerability in Microsoft’s Copilot Studio via a server-side request forgery (SSRF), which allowed researchers access to potentially sensitive information regarding service internals with potential cross-tenant impact. This vulnerability exists due to improper handling of redirect status codes for user-configurable actions within Copilot Studio. This follows the team’s recent discoveries of flaws in Microsoft’s Azure Health Bot service, Azure Service Tags and three vulnerabilities in the Azure API Management service.
Dynatrace Ranked #1 Across Three of Five Use Cases in the 2024 Gartner® Critical Capabilities for Observability Platforms Report
DynatraceGUEST RESEARCH: Dynatrace also named a Leader and positioned furthest for Vision and highest in Execution in the 2024 Gartner Magic Quadrant for Observability Platforms
New SOTI research uncovers critical IT vulnerabilities threatening Australia's emergency services
SOTIGUEST RESEARCH: In the aftermath of the recent CrowdStrike global IT outage, which affected 8.5 million Microsoft Windows devices and led to widespread disruptions in airlines, healthcare providers and retail payment terminals, the fragility of critical infrastructure has come into sharp focus.
New Fastly Threat Research reveals 91% of cyberattacks targeted multiple organisations using mass scanning to uncover and exploit vulnerabilities
FastlyGUEST RESEARCH: Fastly, a leader in global edge cloud platforms, today released the Fastly Threat Insights Report, which found 91% of cyberattacks – up from 69% in 2023 – targeted multiple customers using mass scanning techniques to uncover and exploit software vulnerabilities, revealing an alarming trend in attacks spreading across a broader target base. This new report provides the latest attack trends and techniques across the web application and API security landscape.
APAC organisations increase adoption of AI/ML solutions to address wide range of API security challenges
F5GUEST RESEARCH: APAC organisations are increasingly relying on artificial intelligence and machine learning (AI/ML) enabled solutions to tackle a wide array of security challenges around Application Programming Interfaces (APIs), according to F5’s (NASDAQ: FFIV) inaugural 2024 Strategic Insights: API Security in APAC report. The report examines the challenges and opportunities in API security in Asia Pacific (APAC), as APIs continue to power the region’s digital experiences.
Cohesity Research Finds Organizations Overestimate Their Cyber Resilience, Leading to Business Continuity Issues & Ransom Payments
CohesityGUEST RESEARCH: Cyber resilience research commissioned by Cohesity, a leader in AI-powered data security, reveals organizations overestimate their cyber resilience capabilities and maturity, leading to significant business continuity disruptions and ransom payments.
Stealthy phishing attack uses advanced infostealer for data exfiltration
Barracuda NetworksGUEST RESEARCH: Phishing attacks featuring an advanced, stealthy technique designed to exfiltrate a wide range of sensitive information have been observed by Barracuda threat analysts.
Stealthy phishing attack uses advanced infostealer for data exfiltration – Barracuda research
Barracuda NetworksGUEST RESEARCH: Phishing attacks featuring an advanced, stealthy technique designed to exfiltrate a wide range of sensitive information, according to a new blogpost from Barracuda Networks.
More...
Navigating the future of business travel: Key insights from the 2024 Global Business Traveller Survey
SAP Concur Australia and New ZealandGUEST OPINION: As organisations navigate the challenges of remote work, effective business travel has become crucial, providing opportunities for market expansion, valuable insights, and professional growth. However, new research from SAP Concur highlights the complexities involved in maintaining this essential function. The 2024 Global Business Travel Survey examined trends and challenges faced by 3,750 business travellers and 600 travel managers across global markets in the last year.
BillingPlatform Named a Leader in First-Ever Gartner Magic Quadrant For Recurring Billing Applications
BillingPlatformCOMPANY NEWS: Company Placed Highest in Ability to Execute and Received the Highest Scores in Four of Five Use Cases in the Critical Capabilities report
GUEST RESEARCH: Researchers at Infoblox and Eclypsium have discovered that a powerful attack vector in the domain name system (DNS) is being widely exploited across many DNS providers. We have found that over a dozen Russian-nexus cybercriminal actors are using this attack vector to hijack domain names without being noticed. We call this the Sitting Ducks attack.
New ExtraHop Research Helps Organisations Predict Where Ransomware May Strike Next
ExtraHop
WEBINARS & EVENTS
- UiPath to Unveil Latest Agentic Automation Solutions at Agentic AI Summit
- ALL WELCOME - 6 DAYS TO GO - AI in Action is your opportunity to gain actionable strategies for deploying scalable, reliable AI solutions that drive measurable business outcomes.
- TODAY FREE VIRTUAL EVENT - EXL SERVICE, AI in action Driving the shift to scalable AI
- Expert warns: Small businesses missing out on AI cost-saving and growth opportunities
- Datadog Opens Registration for Its 2025 DASH Conference
CYBERSECURITY
- Nozomi Networks Named to Fast Company’s World’s Most Innovative Companies 2025 List
- Cybersecurity for Small and Medium Businesses in 2025: Challenges and Solutions
- New initiatives to combat SMS scams and build confidence in Australian phone numbers and brands
- Milestone Systems Expands XProtect with Enhanced CLOUD Integration, Advanced Vehicle Analytics
- Fastly Empowers Organisations to Prioritise Security Without Disrupting End-User Experiences
PEOPLE MOVES
- DataSnipper appoints Siu Wei Lee to lead Asia Pacific expansion
- Zetaris, The Modern Lakehouse for AI, Continues its Global Expansion with Appointment of Robert Herjavec as Executive Director Global Strategy
- Wisr Welcomes Inaugural Chief Innovation Officer
- Rubrik Welcomes Sathish Murthy as the Company’s New Field CTO, APJ
- Seeing Machines appoints John Noble as technology chief
GUEST ARTICLES
- Unlock online freedom with a free VPN
- AI and the Future of Insurance: Why Solving the Data Integration Challenge Matters
- What are haplogroups, and how do they connect with ethnicity?
- Why Missouri car accident victims should act fast to protect their legal rights
- What to bring to your first meeting with a Florida personal injury lawyer
- TELETRAC NAVMAN survey finds 83% of fleets say that AI is future of safety
- Workplace Tug-of-War: Organisations Mandate Office Days, But Employees Push for More Flexibility
-
How to prevent tool wear and damage in CNC Aluminum Processing
GUEST OPINION: In the world of precision manufacturing, maintaining the…
- New Trustwave research finds patient lives at risk in healthcare with cybersecurity vulnerabilities
- Anti Scam Investment Much Needed
Guest Opinion
- Unlock online freedom with a free VPN
- AI and the Future of Insurance: Why Solving the Data Integration Challenge Matters
- What are haplogroups, and how do they connect with ethnicity?
- Why Missouri car accident victims should act fast to protect their legal rights
- What to bring to your first meeting with a Florida personal injury lawyer
-
How to prevent tool wear and damage in CNC Aluminum Processing
GUEST OPINION: In the world of precision manufacturing, maintaining the…
- Anti Scam Investment Much Needed
- Govt must Incentivise People Initiatives to Beat Productivity Slump
- Network Technologies Driving Sustainability for Education and Hospitality in 2025
- Transitioning to a new ERP system is like open heart surgery for business
ITWIRETV & INTERVIEWS
- Amazon CISO CJ Moses gives rare interview
- Matt Salier explains the Australian Cyber Collaboration Centre's voluntary data classification framework
- Qualys CEO Sumedh Thakar explains the Risk Operations Centre (ROC)
- iTWire talks to SailPoint about identity management in the Enterprise
- How Blue Yonder is applying AI and innovation to solve supply chain challenges